Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
Search Results For - Linux
shimit is a python tool that implements the Golden SAML attack. python .\shimit.py -h usage: shimit.py [-h] -pk KEY [-c CERT] [-sp SP] -idp IDP -u USER [-reg...
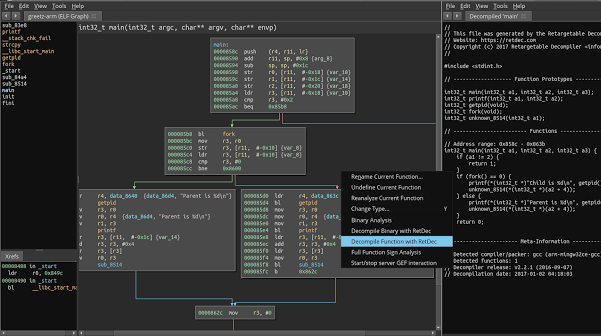
RetDec is a retargetable machine-code decompiler based on LLVM. The decompiler is not limited to any particular target architecture, operating system, or...
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
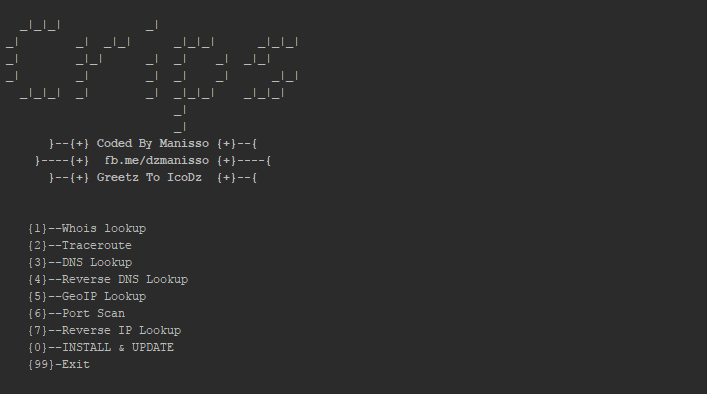
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois...
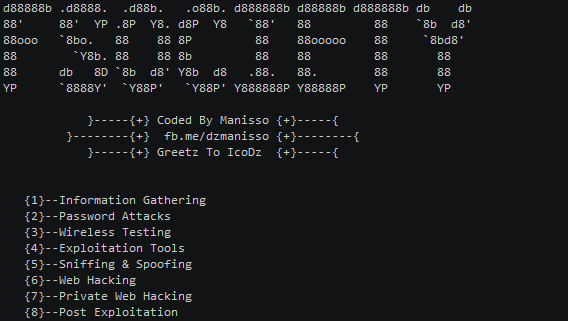
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
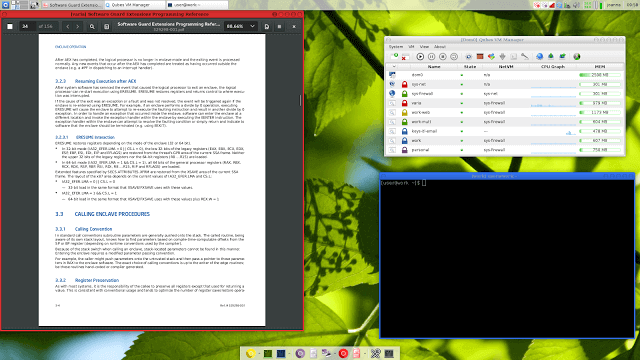
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
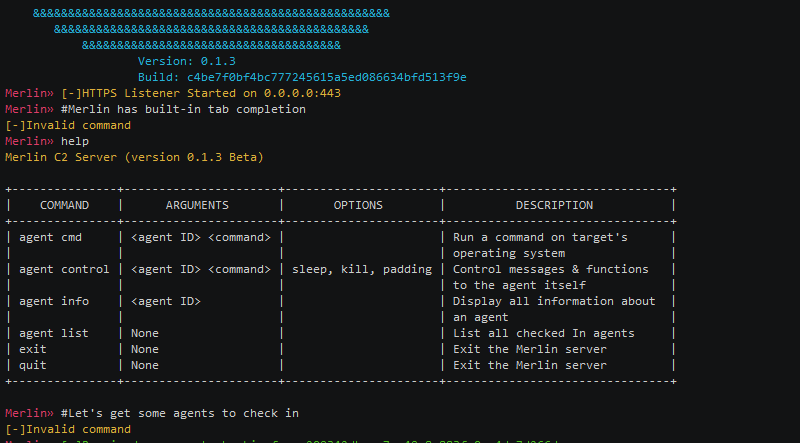
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
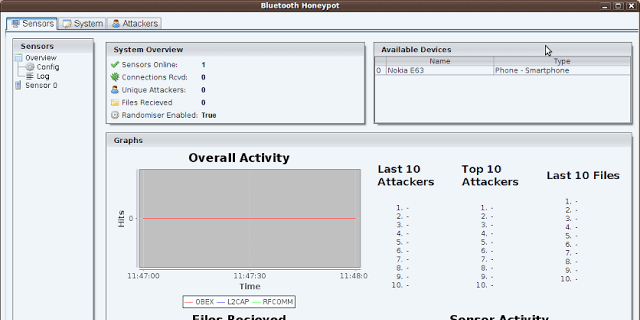
This code is from a University Project written in 2010. This is a newer version of the code than is on Google Code. Bluepot is a Bluetooth Honeypot written in...
A script for installing and automatically configuring DNSCrypt on Linux-based systems. Description DNSCrypt is a protocol for securing communications between a...