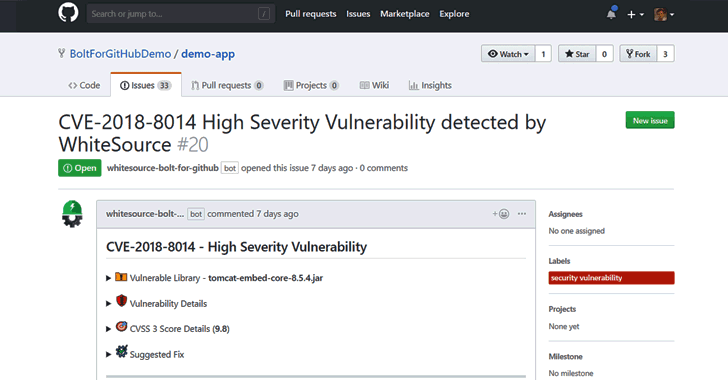
[sc name=”ad_1″] Developers around the world depend on open source components to build their software products. According to industry estimates...
Search Results For - Information
[sc name=”ad_1″] Cybersecurity researchers have discovered a new zero-day vulnerability in Adobe Flash Player that hackers are actively exploiting...
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
Looking for an automated malware analysis software? Something like a 1-click solution that doesn’t require any installation or configuration…a...
Tested on Kali Linux. Should work with all Debian based distros (and other ones if you have the right packages installed) BabySploit is a penetration testing...
Manticore is a symbolic execution tool for analysis of binaries and smart contracts. Note: Beginning with version 0.2.0, Python 3.6+ is required. Features...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
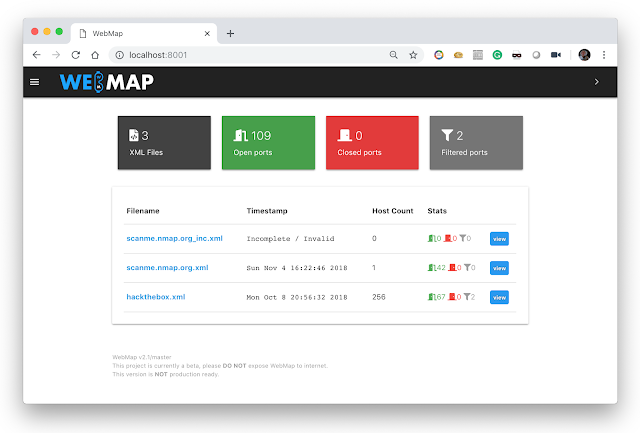
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
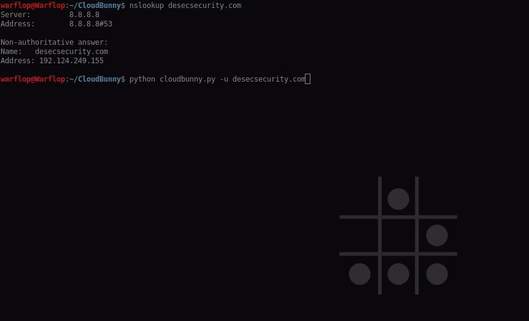
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
Pacu is an open source AWS exploitation framework, designed for offensive security testing against cloud environments. Created and maintained by Rhino Security...