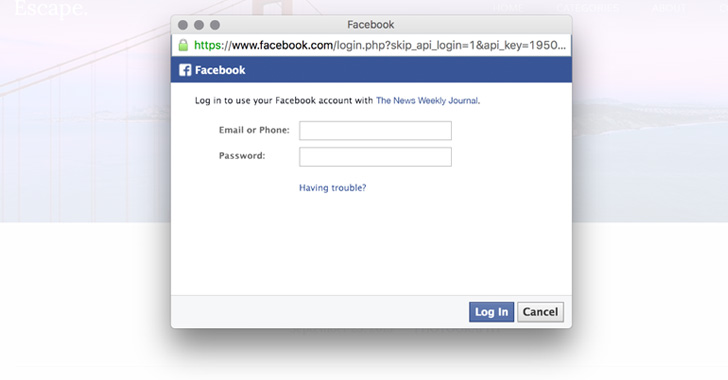
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
Search Results For - Information
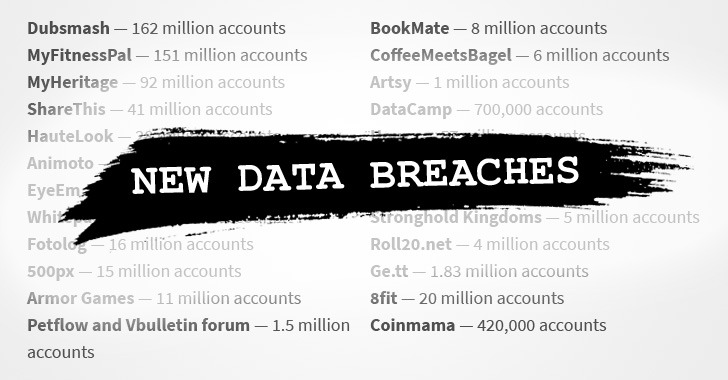
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second...
[sc name=”ad_1″] The United States Department of Justice has announced espionage charges against a former US Air Force intelligence officer with...
[sc name=”ad_1″] Justniffer is a network protocol analyzer that captures network traffic and produces logs in a customized way, can emulate Apache...
[sc name=”ad_1″] Welcome back! Adobe has today released its monthly security updates to address a total of 75 security vulnerabilities across its...
[sc name=”ad_1″] Microsoft has issued its second Patch Tuesday for this year to address a total of 77 CVE-listed security vulnerabilities in its...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
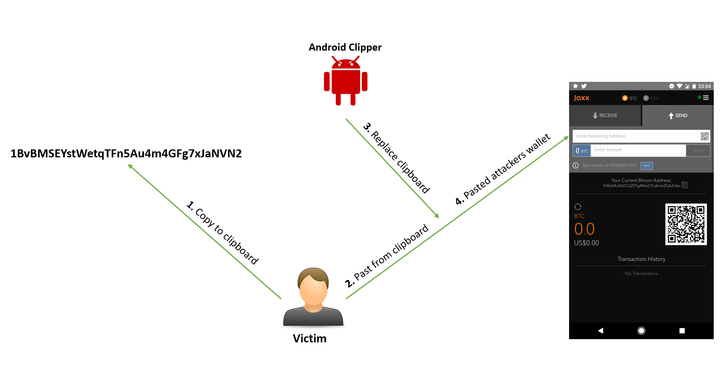
[sc name=”ad_1″] A security researcher has discovered yet another cryptocurrency-stealing malware on the official Google Play Store that was...
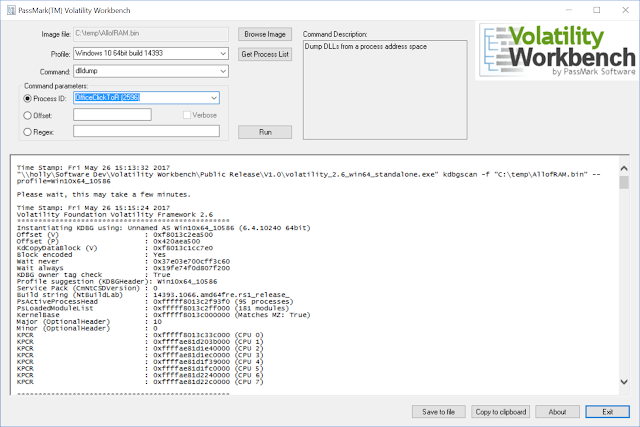
[sc name=”ad_1″] Volatility Workbench is a graphical user interface (GUI) for the Volatility tool. Volatility is a command line memory analysis and...
[sc name=”ad_1″] Google has launched a new encryption algorithm that has been built specifically to run on mobile phones and smart IoT devices that...