[sc name=”ad_1″] The developers behind the privacy-minded Zcash cryptocurrency have recently discovered and patched a highly dangerous...
Search Results For - Hidden
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...
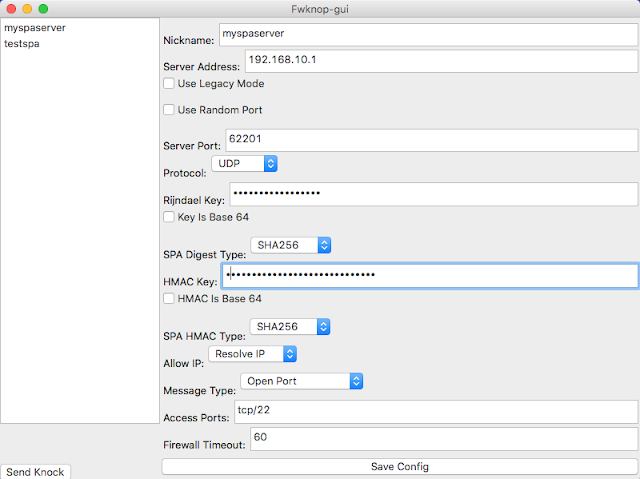
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
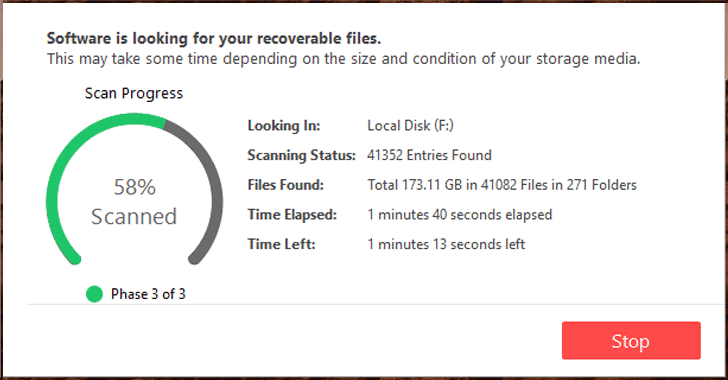
[sc name=”ad_1″] Have you ever lost your important files, like memories or official documents, accidentally or maliciously? Adding more… when...
[sc name=”ad_1″] A set of 36-year-old vulnerabilities has been uncovered in the Secure Copy Protocol (SCP) implementation of many client...
[sc name=”ad_1″] Google has removed 85 apps from its Play Store after finding out that they were pushing aggressive, full-screen adware to Android...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...
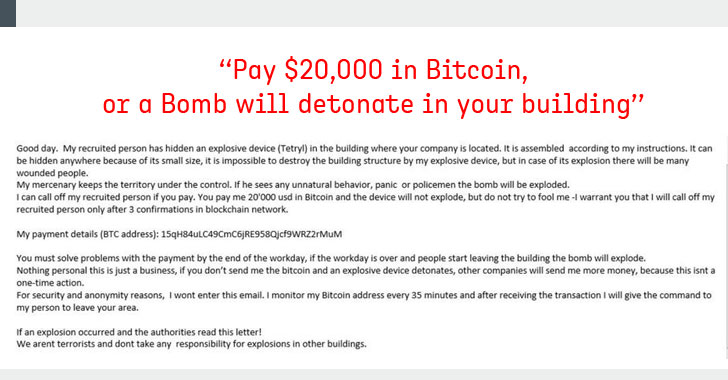
[sc name=”ad_1″] “Pay $20,000 worth of bitcoin, or a bomb will detonate in your building” A massive number of businesses, schools...