It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Search Results For - Hacking
This hack was not conducted in a laboratory, but on a 757 gathered at the airport in Atlantic City, N.J. And the real hack happened over a year ago. We are...
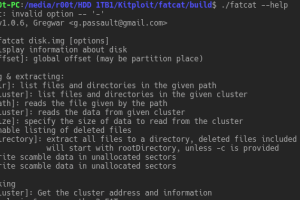
This tool is designed to manipulate FAT filesystems, in order to explore, extract, repair, recover and forensic them. It currently supports FAT12, FAT16 and...
News of the event was posted on Twitter by vigilante hacker, “The Jester,” who has in the past increased fame by hacking jihadist websites, and who in October...
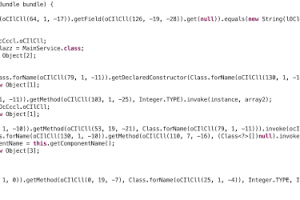
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
The Trump Organization dismissed the domain names were ever Hacked. But a review of internet credentials by the AP and cybersecurity specialists shows...
Diamorphine is a LKM rootkit for Linux Kernels 2.6.x/3.x/4.x Features When loaded, the module starts invisible; Hide/unhide any process by sending a signal 31;...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
The British government has admitted publicly for the first time that it is all but certain North Korea carried out the “WannaCry” malware attack...