Newly uncovered vulnerabilities in a popular brand of indoor internet-connected cameras could be exploited by attackers in order to gain complete control of...
Search Results For - Firmware
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
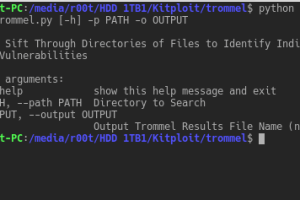
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
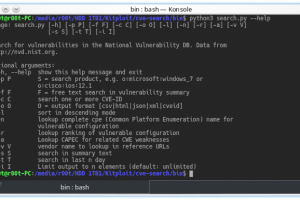
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...