ADRecon is a tool which extracts various artifacts (as highlighted below) out of an AD environment in a specially formatted Microsoft Excel report that...
Search Results For - File Include
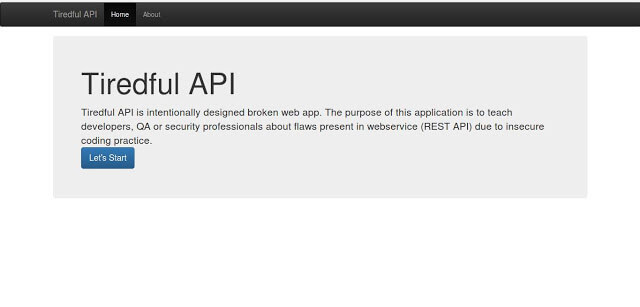
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
The maker of a sneaky adware that hijacks a user’s browser to serve ads is back with a new, more advanced version — one that can gain root...
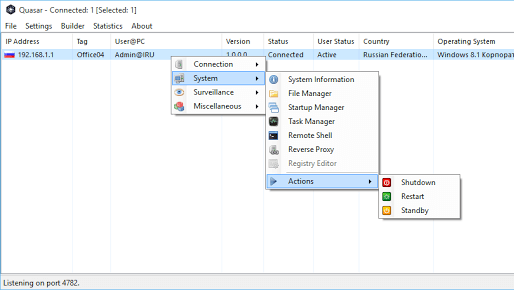
Quasar is a fast and light-weight remote administration tool coded in C#. Providing high stability and an easy-to-use user interface, Quasar is the perfect...
Even software that has been built with secure development procedures may still be vulnerable to attack, due to flaws in the interpreted programming languages...
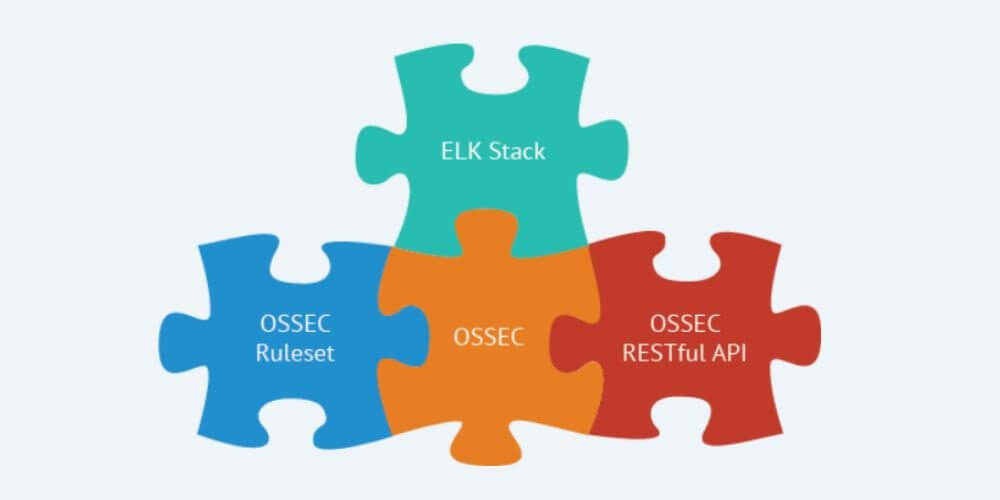
Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and...
Aletheia is a steganalysis tool for the detection of hidden messages in images. The goal of steganalysis is to identify suspected packages, determine whether...
Denis Sinegubko (a security researcher from Sucuri) has discovered a new wave of the known malware wp-vcd that injects malicious WordPress admin users into...
The keylogging code was embedded in the SynTP.sys file, which is a module of the Synaptics Touchpad driver that ships with HP notebook models. “The logging was...
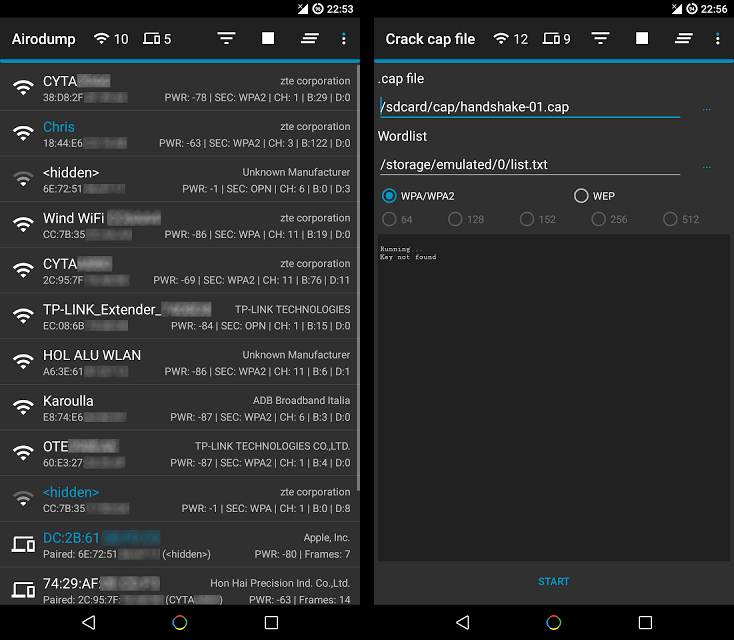
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these...