The malicious software uncovered pornographic ads and attempted to trick users into buying added services, according to Check Point. “We’ve eliminated the apps...
Search Results For - Discover
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
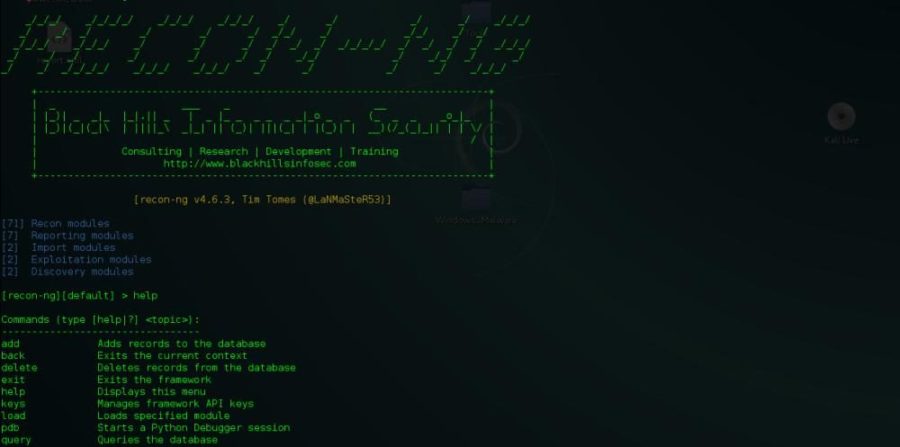
Recon-ng is a full-featured Web Reconnaissance framework written in Python. Complete with independent modules, database interaction, built in convenience...
Apple has issued a statement regarding the Meltdown and Spectre vulnerabilities, confirming all Mac systems and iOS devices are affected, but saying there are...
At last, Wi-Fi security — or lack of — is about to get its day in the sun. The Wi-Fi Alliance, an industry body made up of device makers including...
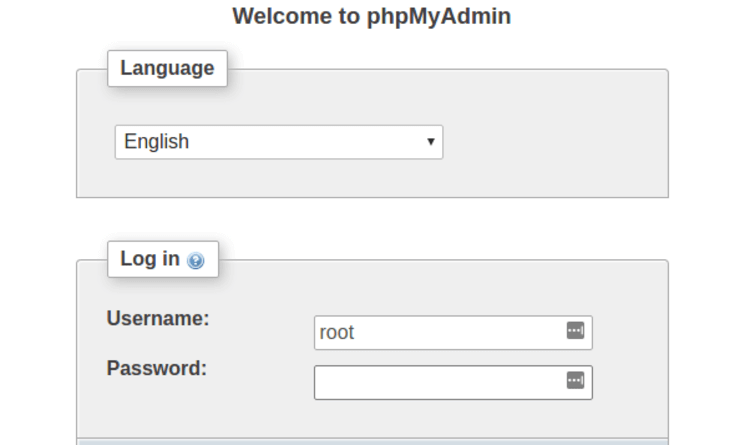
Amongst the most common and in demand applications for MySQL database management is the phpMyAdmin, which became vulnerable, when a critical flaw was found in...
One of the biggest names in IT industry, Intel, has verified a report stating that some microprocessors have been built containing flaws in their design...
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
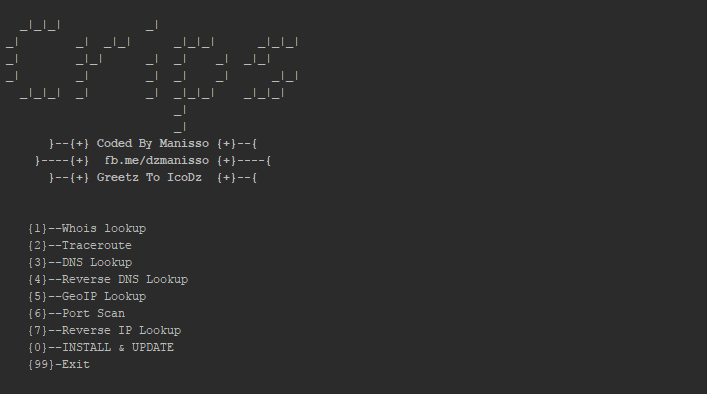
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois...
Russian ATMs Are Hackable It was recently revealed that some ATMs that are running in Russia are still operating on Windows XP operating system, which is why...