[sc name=”ad_1″] A vulnerability scanner for container images and filesystems. Easily install the binary to try it out. Features Scan the contents...
Search Results For - Database Files
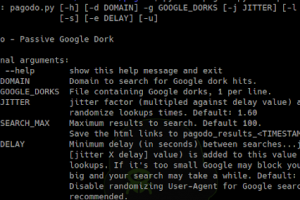
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...
[sc name=”ad_1″] Security researchers have discovered two high-severity vulnerabilities in the SHAREit Android app that could allow attackers to...
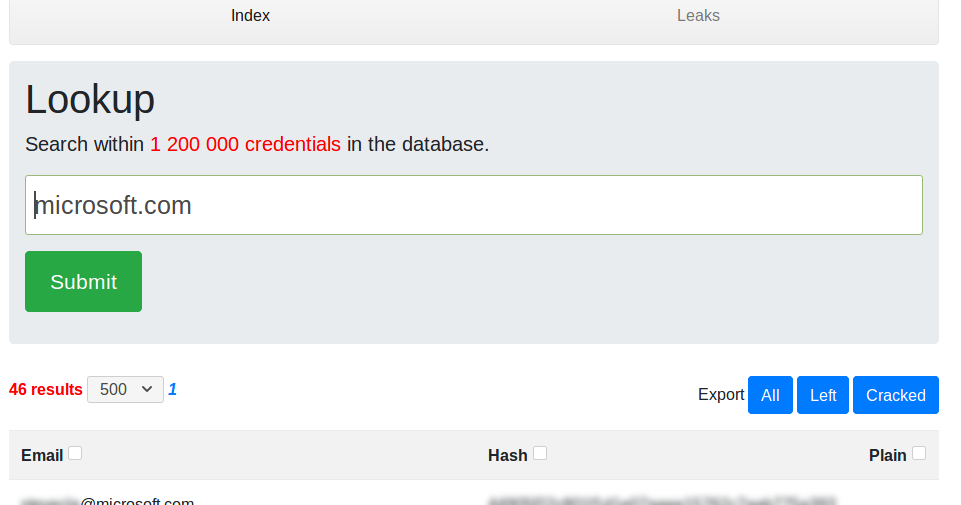
LeakScraper is an efficient set of tools to process and visualize huge text files containing credentials. These tools are designed to help...
ODAT (Oracle Database Attacking Tool) is an open source penetration testing tool that tests the security of Oracle Databases remotely. Usage examples of ODAT:...
MSDAT (Microsoft SQL Database Attacking Tool) is an open source penetration testing tool that tests the security of Microsoft SQL Databases remotely. Usage...
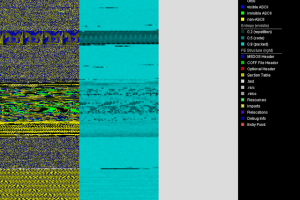
PortEx is a Java library for static malware analysis of Portable Executable files. Its focus is on PE malformation robustness, and anomaly detection. PortEx is...
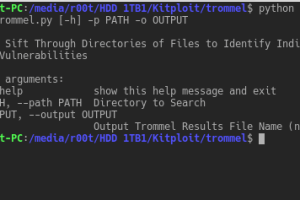
TROMMEL sifts through directories of files to identify indicators that may contain vulnerabilities. TROMMEL identifies the following indicators related to:...
[sc name=”ad_1″] BigBountyRecon tool utilises 58 different techniques using various Google dorks and open source tools to expedite the process of...
[sc name=”ad_1″] SARENKA is an Open Source Intelligence (OSINT) tool which helps you obtaining and understanding Attack Surface. The main goal is...