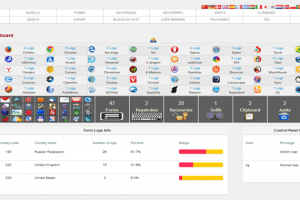
This project aims at delivering browser exploits to the victim browser in an encrypted fashion. Ellyptic-curve Diffie-Hellman (secp256k1) is used for key...
Search Results For - Cyber
It seems sophisticated hackers have changed the way they conduct targeted cyber operations—instead of investing in zero-days and developing their malware; some...
A BLE scanner for “smart” devices hacking based on the bluepy library, dead easy to use because retarded devices should be dead easy to hack. How to...