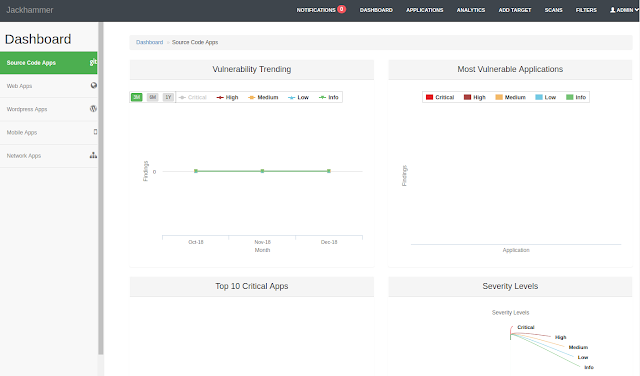
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
Search Results For - Credentials
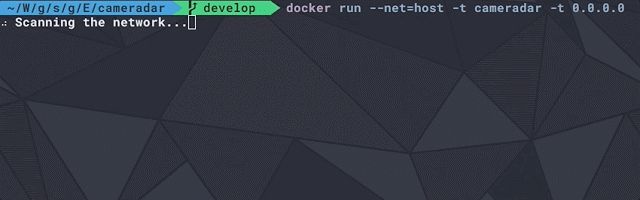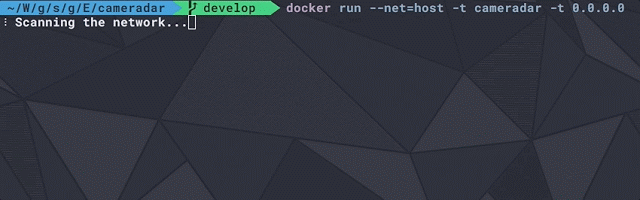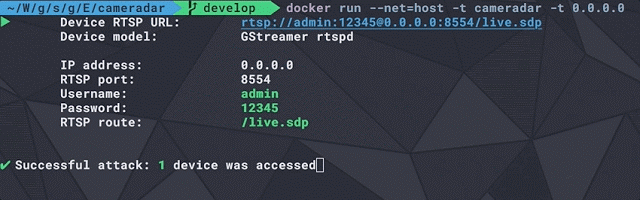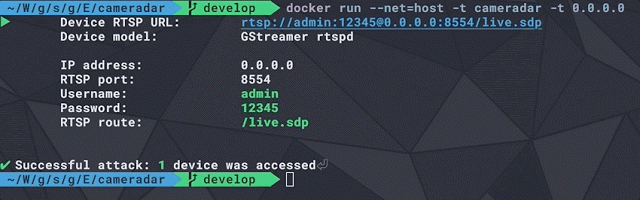
[sc name=”ad_1″] An RTSP stream access tool that comes with its library Cameradar allows you to Detect open RTSP hosts on any accessible target...
[sc name=”ad_1″] Developers of phpMyAdmin, one of the most popular and widely used MySQL database management systems, today released an updated...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
[sc name=”ad_1″] The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and...
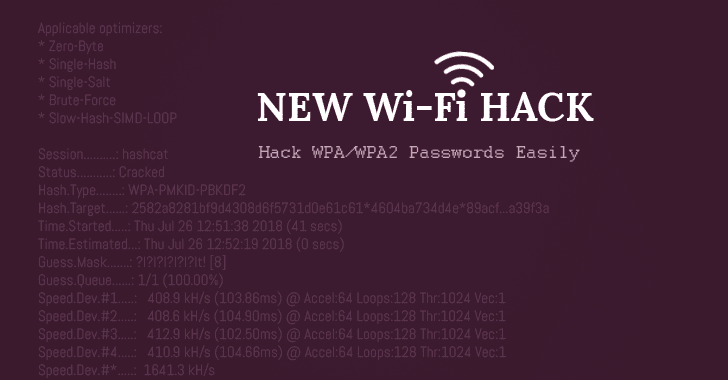
[sc name=”ad_1″] Looking for how to hack WiFi password OR WiFi hacking software? Well, a security researcher has revealed a new WiFi hacking...
A new piece of ransomware is spreading rapidly across China that has already infected more than 100,000 computers in the last four days as a result of a supply...
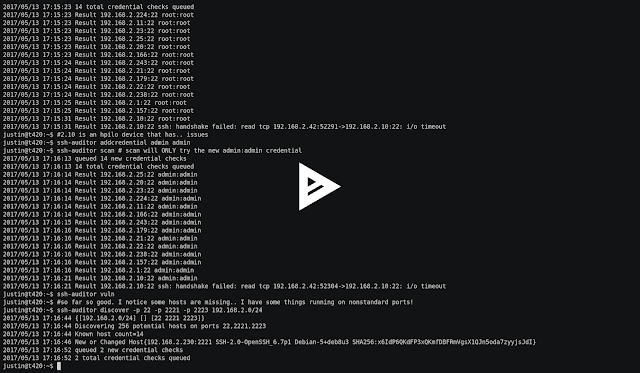
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
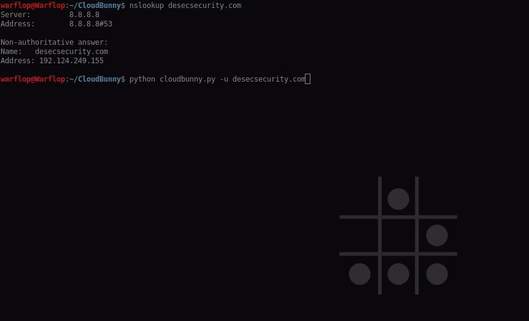
CloudBunny is a tool to capture the real IP of the server that uses a WAF as a proxy or protection. How works In this tool we used three search engines to...
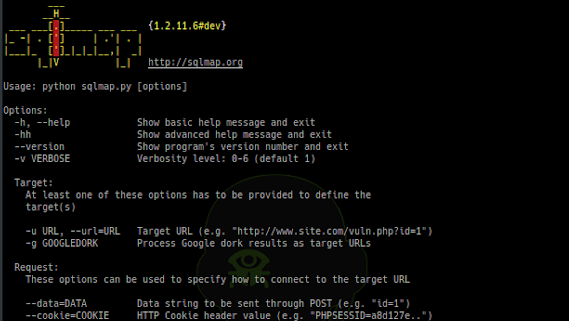
SQLMap is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database...