It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Search Results For - Control
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of...
This hack was not conducted in a laboratory, but on a 757 gathered at the airport in Atlantic City, N.J. And the real hack happened over a year ago. We are...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
The tool itself is impressive enough, serving as the backbone of the CIA’s malware processes, but there’s more. What’s interesting about the first leak in the...
Security firm Positive Technologies lists being able to execute unsigned code on computers working the IME through USB. The fully fleshed-out details of the...
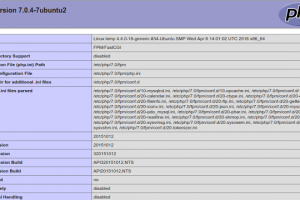
Check current PHP configuration for potential security flaws. Simply access this file from your webserver or run on CLI. Author This software was written by...
Oracle Identity Manager (OIM) allows companies to manage the entire user life-cycle overall company resources both within and behind a firewall. Within Oracle...
Onion Routed Cloud is a decentralized, anonymous, object storage platform owned and operated by allies in defense of human rights and opposition to censorship...