[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...
Search Results For - Control
[sc name=”ad_1″] Microsoft has issued its first Patch Tuesday for this year to address 49 CVE-listed security vulnerabilities in its Windows...
[sc name=”ad_1″] Google has removed 85 apps from its Play Store after finding out that they were pushing aggressive, full-screen adware to Android...
[sc name=”ad_1″] Popular cryptocurrency exchange Coinbase has suspended all transactions of Ethereum Classic (ETC)—the original unforked version of...
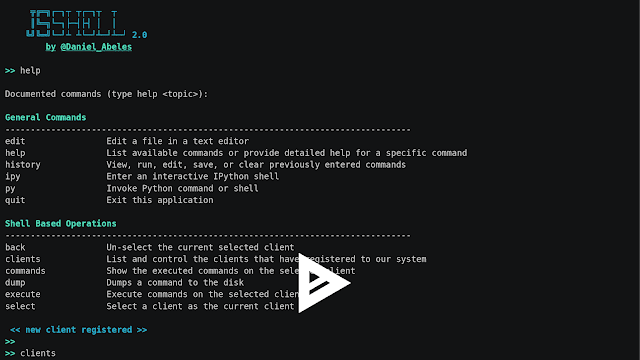
[sc name=”ad_1″] An interactive multi-user web based javascript shell. It was initially created in order to debug remote esoteric browsers during...
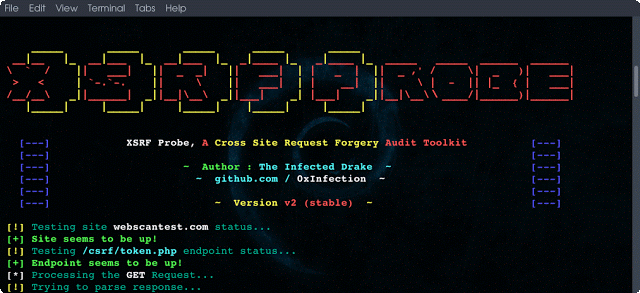
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
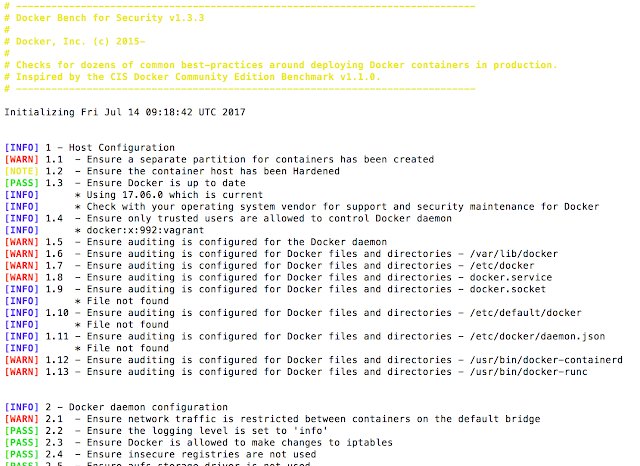
[sc name=”ad_1″] The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in...
[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
[sc name=”ad_1″] Another day, another data breach. This time it’s the United States National Aeronautics and Space Administration (NASA) NASA...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...