[sc name=”ad_1″] Terrier is a Image and Container analysis tool that can be used to scan OCI images and Containers to identify and verify the...
Search Results For - Configuration
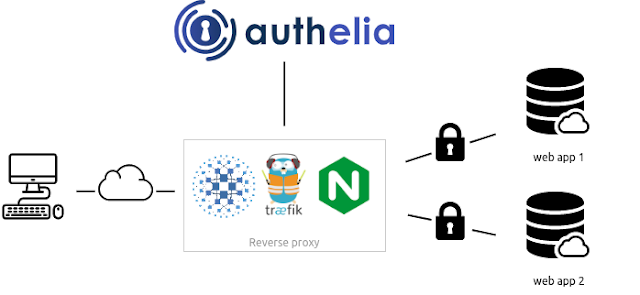
[sc name=”ad_1″] Authelia is an open-source authentication and authorization server providing 2-factor authentication and single sign-on (SSO) for...
[sc name=”ad_1″] SkyWrapper is an open-source project which analyzes behaviors of temporary tokens created in a given AWS account. The tool is...
[sc name=”ad_1″] Stupidly easy to use, small footprint Policy as Code subsecond command-line scanner that leverages the power of the fastest multi...
[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual...
[sc name=”ad_1″] RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently...
[sc name=”ad_1″] by Gabriel Ryan (s0lst1c3)(gryan[at]specterops.io) EAPHammer is a toolkit for performing targeted evil twin attacks against WPA2...
[sc name=”ad_1″] These files contain configuration for producing EDR (endpoint detection and response) data in addition to standard system logs...