[sc name=”ad_1″] Sherlock, a powerful command line tool provided by Sherlock Project, can be used to find usernames across many social networks. It...
Search Results For - Command Line
[sc name=”ad_1″] A security testing tool to facilitate GraphQL technology security auditing efforts. InQL can be used as a stand-alone script or as...
[sc name=”ad_1″] ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will...
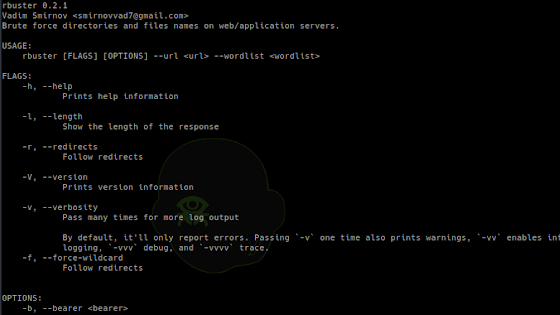
[sc name=”ad_1″] yet another dirbuster Common Command line options -a <user agent string> – specify a user agent string to send in the...
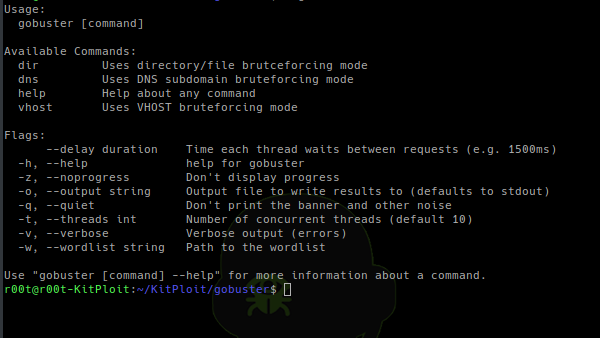
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual...
[sc name=”ad_1″] RITA is an open source framework for network traffic analysis. The framework ingests Bro/Zeek Logs in TSV format, and currently...
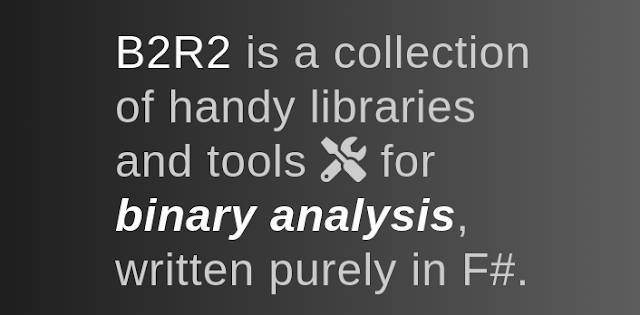
[sc name=”ad_1″] B2R2 is a collection of useful algorithms, functions, and tools for binary analysis, written purely in F# (in .NET lingo, it is...
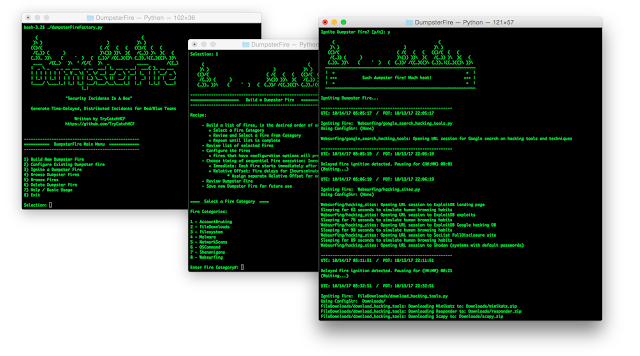
[sc name=”ad_1″] DumpsterFire Toolset – “Security Incidents In A Box!” The DumpsterFire Toolset is a modular, menu-driven, cross...
[sc name=”ad_1″] FAT is a toolkit built in order to help security researchers analyze and identify vulnerabilities in IoT and embedded device...
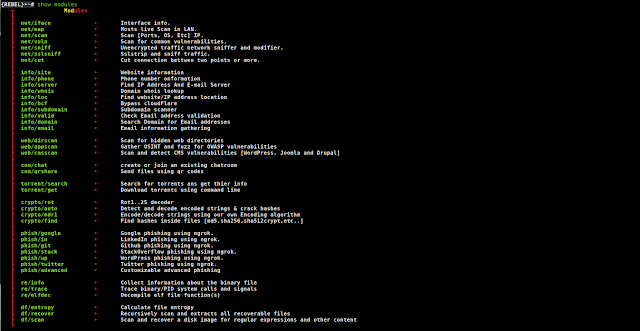
[sc name=”ad_1″] Rebel framework is an advanced and easy to use penetration testing framework.You can use it to automate the automation itself...