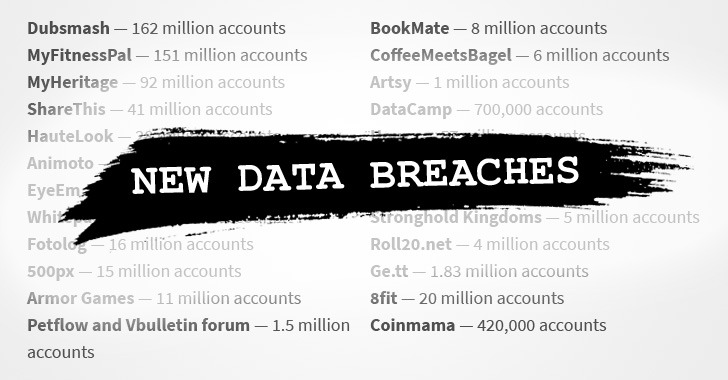
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second...
Search Results For - Cloud
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
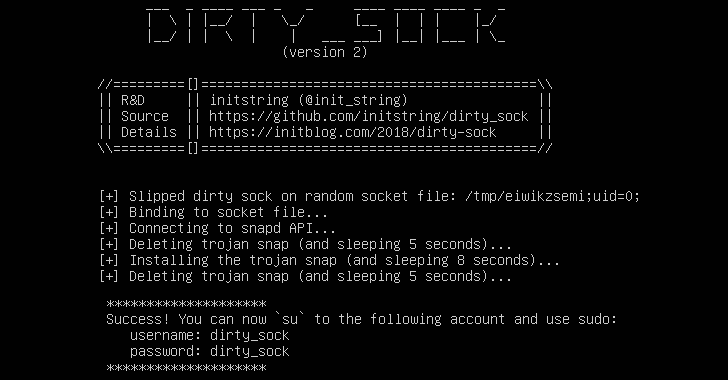
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
[sc name=”ad_1″] Welcome back! Adobe has today released its monthly security updates to address a total of 75 security vulnerabilities across its...
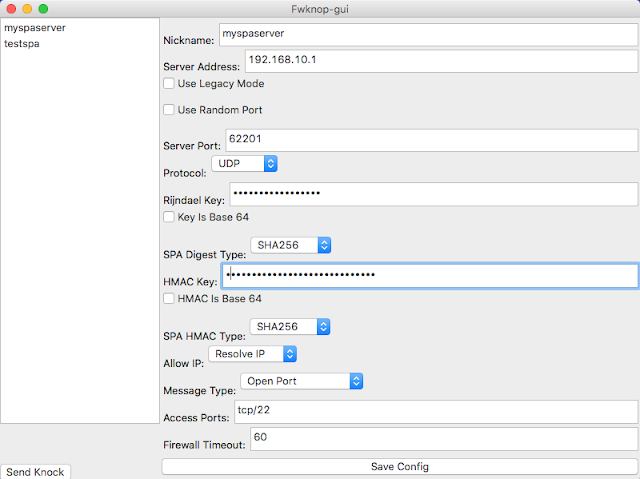
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] A California-based Voice-Over-IP (VoIP) services provider VOIPO has accidentally left tens of gigabytes of its customer data...
[sc name=”ad_1″] Almost every activity on the Internet starts with a DNS query, a key function of the Internet that works as an Internet’s...
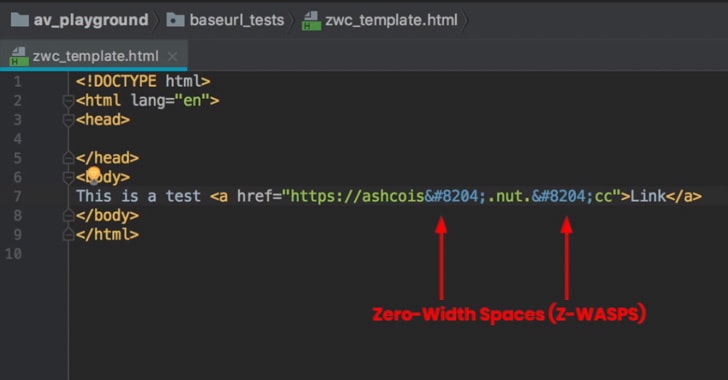
[sc name=”ad_1″] Security researchers have been warning about a simple technique that cybercriminals and email scammers are already being using in...
[sc name=”ad_1″] The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous...
[sc name=”ad_1″] Security researchers have discovered yet another example of how cybercriminals disguise their malware activities as regular...