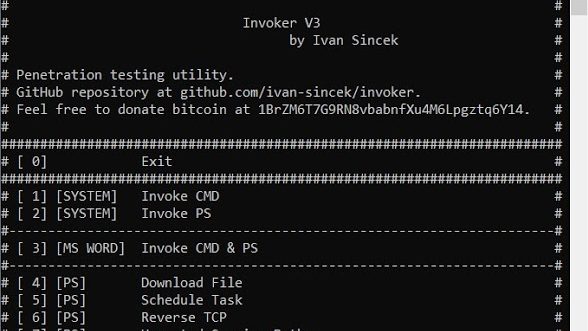
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...
Search Results For - Antivirus
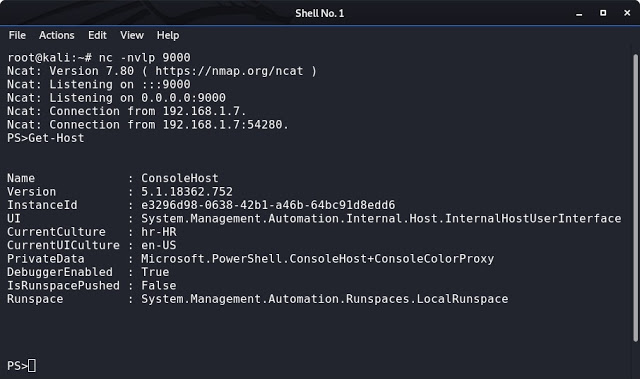
[sc name=”ad_1″] PowerShell script for connecting to a remote host. Remote host will have full control over client’s PowerShell and all its...
[sc name=”ad_1″] Various cyber criminal groups and individual hackers are still exploiting a recently patched critical code execution vulnerability...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
[sc name=”ad_1″] Just because an app is available on Google Play Store doesn’t mean that it is a legitimate app. Despite so many efforts by...
[sc name=”ad_1″] The United States Department of Justice (DoJ) announced Wednesday its effort to “map and further disrupt” a botnet...
[sc name=”ad_1″] Since most security tools also keep an eye on the network traffic to detect malicious IP addresses, attackers are increasingly...
[sc name=”ad_1″] A massive government data belonging to the Oklahoma Department of Securities (ODS) was left unsecured on a storage server for at...
[sc name=”ad_1″] Remember “The Shadow Brokers” and the arrest of a former NSA contractor accused of stealing 50 Terabytes of top secret...
[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...