A new widespread ransomware worm, known as “Bad Rabbit,” that hit over 200 major organisations, primarily in Russia and Ukraine this week leverages...
Search Results For - Analysis
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...
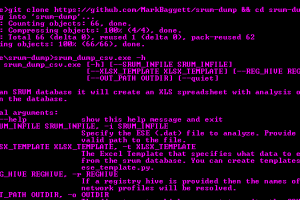
srum-dump This program will create an excel spreadsheet containing forensics artifacts contained the SRUM (System Resource Utilization Manager) database. The...
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned...
Rather than heavily protecting backdoors with hardcore packers, many malware authors evade heuristic detections by obfuscating only key portions of an...
Joe Belfiore continued that he had also shifted to Android himself. Windows 10 Mobile attempted to attract users by making them run the same “universal apps”...
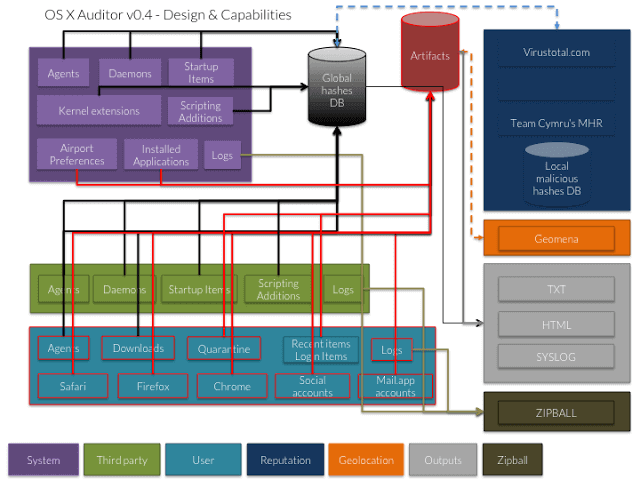
OS X Auditor is a free Mac OS X computer forensics tool. OS X Auditor parses and hashes the following artifacts on the running system or a copy of a system you...
Habu is to teach (and learn) some concepts about Python and Network Hacking. These are basic functions that help with some tasks for Ethical Hacking and...
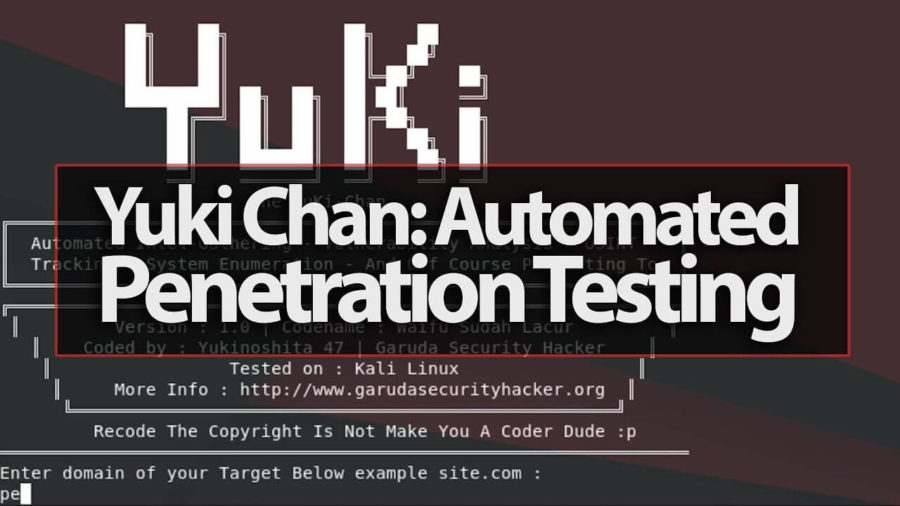
Hey Guys, In this video i show you a great tool called Yuki Chan. The Yuki Chan is an Automated Penetration Testing tool this tool will auditing all standard...