[sc name=”ad_1″] It is utmost important for any security engineer to understand their network first before securing it and it becomes a daunting...
Search Results For - Analysis
[sc name=”ad_1″] Introduction Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of...
[sc name=”ad_1″] Phishing Simulation mainly aims to increase phishing awareness by providing an intuitive tutorial and customized assessment...
[sc name=”ad_1″] Popular enterprise software company Citrix that provides services to the U.S. military, the FBI, many U.S. corporations, and...
[sc name=”ad_1″] You must update your Google Chrome immediately to the latest version of the web browsing application. Security researcher Clement...
[sc name=”ad_1″] Google’s one-year-old cybersecurity venture Chronicle today announced its first commercial product, called Backstory, a...
[sc name=”ad_1″] Security researchers have finally, with “high confidence,” linked a previously discovered global cyber espionage...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
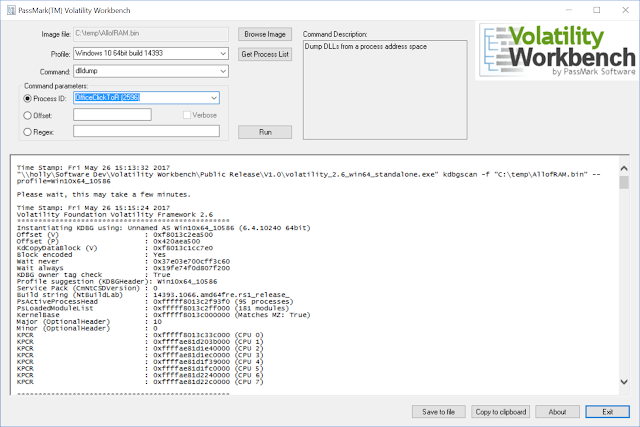
[sc name=”ad_1″] Volatility Workbench is a graphical user interface (GUI) for the Volatility tool. Volatility is a command line memory analysis and...
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...