Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
Search Results For - Access
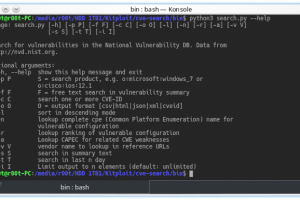
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected...
A convention in Athens, Greece, Munro detailed some of the appalling security lapses Pen Test Partners found while investigating naval ships that had things...
ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned...
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of...
Security researchers from AccessNow have discovered a new Facebook phishing scam that can also fool a professional technical user into falling victim to this...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more)...
An RTSP stream access tool that comes with its library. Cameradar allows you to Detect open RTSP hosts on any accessible target host Detect which device model...
Israel told the NSA, where frightened officials quickly began a hunt for the gap, according to users familiar with the subject, who said an inquiry by the...