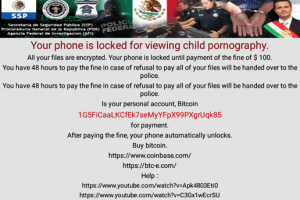
Security researchers from SfyLabs have detected an Android banking trojan dubbed LokiBot that transforms itself into a complete ransomware once the targeted...
Search Results For - Access
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
Wesley Neelen (security researcher) has received a phishing email that seems to be from the legal online Ethereum wallet site Myetherwallet.com. Cybercriminals...
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...
According to various cybersecurity firms, the growing virus is dubbed “BadRabbit” and is a form of ransomware that bolts down machines and requires bitcoin...
81 percent of data breaks last year involved weak, default or stolen passwords, and phishing attacks have advanced 65 percent year-on-year. Protecting online...
In an astonishing hit to the Darknet, four of it’s most popular marketplaces all went down at the same time. Marketplaces involved include Tochka, Wall Street...
DNS over TLS is a protocol where DNS inquiries will be encrypted to the equivalent level as HTTPS and therefore a DNS can’t actually log or see the websites...