[sc name=”ad_1″] It seems as though not a day goes by without a new story breaking about a high-level cyber attack on a major corporation or...
Search Results For - AES 256
The best gaming laptops and the best laptops were almost indistinguishable, few years ago. As long as you had an Intel Core i7 processor, 8GB of RAM and...
Evil Remote Administration Tool (RAT) for macOS/OS X Features Emulate a terminal instance Simple extendable module system No bot dependencies (pure python)...
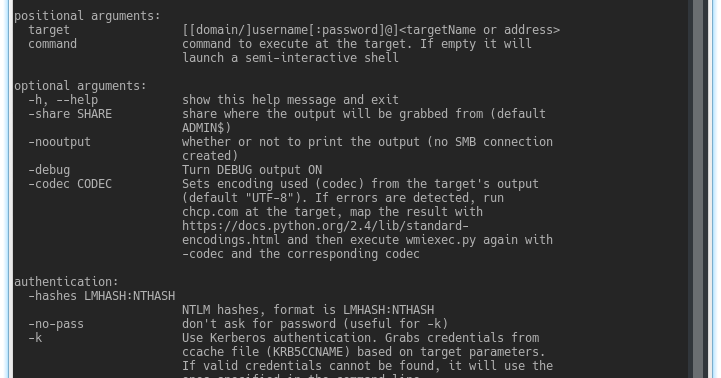
Impacket is a collection of Python classes for working with network protocols. Impacket is focused on providing low-level programmatic access to the packets...
Simple TCP reverse shell written in Go. It uses TLS to secure the communications, and provide a certificate public key fingerprint pinning feature, preventing...
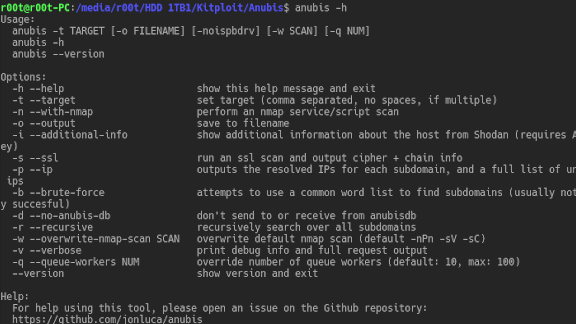
Anubis is a subdomain enumeration and information gathering tool. Anubis collates data from a variety of sources, including HackerTarget, DNSDumpster, x509...
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
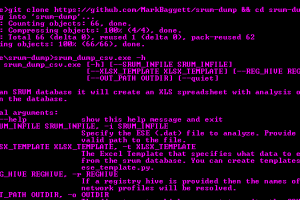
srum-dump This program will create an excel spreadsheet containing forensics artifacts contained the SRUM (System Resource Utilization Manager) database. The...
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...