[sc name=”ad_1″] A low interaction honeypot with the capability to be more of a medium interaction honeypot. HoneyPy is written in Python2 and is intended to...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high and 5 feet...
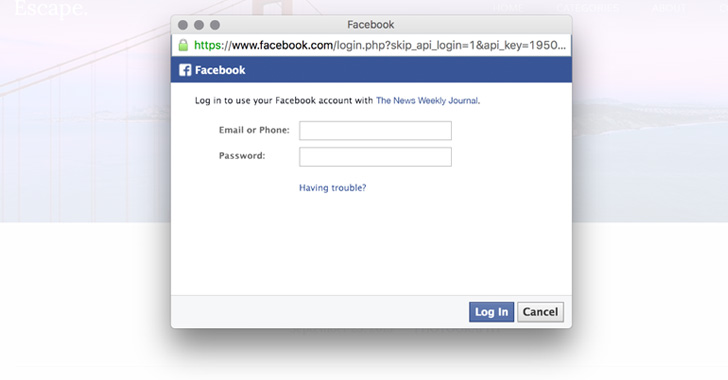
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without any...
[sc name=”ad_1″] Wohooo! Great news for hackers and penetration testers. Offensive Security has just released Kali Linux 2019.1, the first 2019 version of...
[sc name=”ad_1″] It’s not at all surprising that downloading movies and software from the torrent network could infect your computer with malware, but...
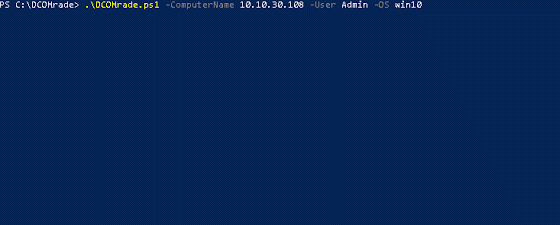
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for lateral...
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By checking if the...
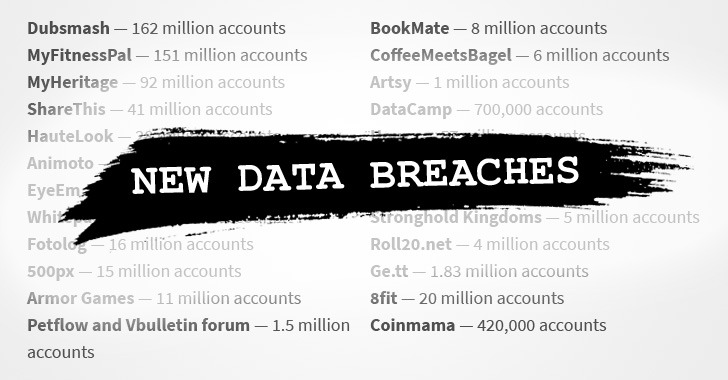
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second batch of 127...
[sc name=”ad_1″] The United States Department of Justice has announced espionage charges against a former US Air Force intelligence officer with the highest...
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container management...