srum-dump This program will create an excel spreadsheet containing forensics artifacts contained the SRUM (System Resource Utilization Manager) database. The program can...
DNS over TLS is a protocol where DNS inquiries will be encrypted to the equivalent level as HTTPS and therefore a DNS can’t actually log or see the websites you visit...
The cryptocurrency hit an all-time high of $6,147.07 just a time after forcing through the $6,000 mark, according to data from application website CoinDesk. Much of the...
Now, Google has declared that AutoML has defeated the human AI engineers at their own game by setting machine-learning software that’s more effective and powerful than...
Burp Suite extension is able to find reflected XSS on page in real-time while browsing on web-site and include some features as: Highlighting of reflection in the...
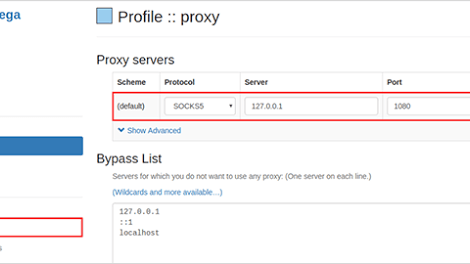
A wrapper tool for shadowsocks to consistently bypass firewalls. Quick start Automatically connect The easiest way to run this tool is just type ssct in terminal, and...
One stop tool for auditing the security posture of AWS. Pre-requisites Python 2.7 pip git Installation git clone cd cs-suite/ sudo python setup.py Note – Generate...
Bash script purposed for system enumeration, vulnerability identification and privilege escalation. MIDA Multitool draws functionality from several of my previous...
Just a year after Mirai—biggest IoT-based malware that caused vast Internet outages by launching massive DDoS attacks—completed its first anniversary, security...
The motion seeks to make it more stressful for students to cheat in exams. As a section of the new rules, schools will also be allotted to do history checks on students’...