[sc name=”ad_1″]
PA Toolkit is a collection of traffic analysis plugins to extend the functionality of Wireshark from a micro-analysis tool and protocol dissector to the macro analyzer and threat hunter. PA Toolkit contains plugins (both dissectors and taps) covering various scenarios for multiple protocols, including:
- WiFi (WiFi network summary, Detecting beacon, deauth floods etc.)
- HTTP (Listing all visited websites, downloaded files)
- HTTPS (Listing all websites opened on HTTPS)
- ARP (MAC-IP table, Detect MAC spoofing and ARP poisoning)
- DNS (Listing DNS servers used and DNS resolution, Detecting DNS Tunnels)
The project is under active development and more plugins will be added in near future.
This material was created while working on “Traffic Analysis: TSHARK Unleashed” course. Those interested can check the course here: https://www.pentesteracademy.com/course?id=42
Installation
Steps:
- Copy the “plugins” directory to Wireshark plugins directory.
- Start wireshark. 🙂
One can get the location of wireshark plugins directory by checking Help > About Wireshark > Folders
- Blackhat Arsenal 2018 <https://www.blackhat.com/us-18/arsenal/schedule/index.html#pa-toolkit-wireshark-plugins-for-pentesters-12035>
- DEF CON 26 Demolabs <https://defcon.org/html/defcon-26/dc-26-demolabs.html>
- Nishant Sharma, Technical Manager, Pentester Academy <[email protected]>
- Jeswin Mathai, Security Researcher, Pentester Academy <[email protected]>
Under the guidance of Mr. Vivek Ramachandran, CEO, Pentester Academy
Documentation
For more details refer to the “PA-Toolkit.pdf” PDF file. This file contains the slide deck used for presentations.
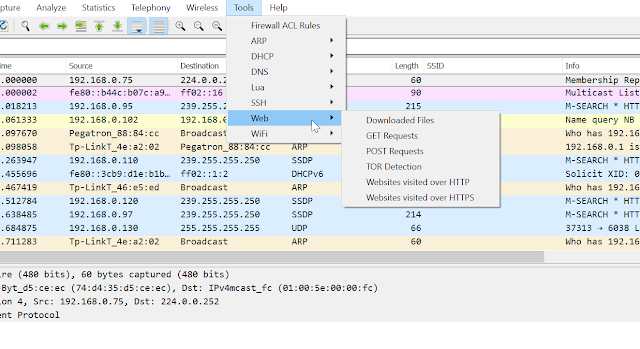
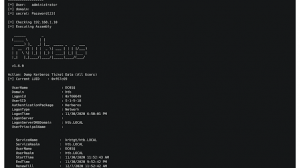
Screenshots
PA Toolkit after installation
List of websites visited over HTTP
Search functionality
Domain to IP mappings






















Add Comment