The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has likely been using the malware since 2016 to target the aerospace, telecommunications, and finance industries.
The alert — issued jointly by the FBI and the US Computer Emergency Readiness Team (US-CERT), which is part of the Department of Homeland Security (DHS) — identifies IP addresses that North Korean actors are suspected of using to maintain a presence on victims’ networks. The agencies warned of “severe impacts” from successful intrusions, including the loss of proprietary information and operational disruptions.
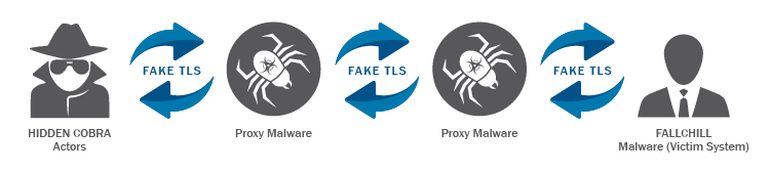
FALLCHILL, the alert said, is issued from a command and control (C2) server to a victim’s system using multiple proxies to obfuscate network traffic. It uses fake Transport Layer Security (TLS) communications, encoding the data with RC4 encryption. The picture below illustrates how it works (the US government refers to malicious cyber activity by the North Korean government as HIDDEN COBRA):
The malware typically infects a system as a file dropped by other North Korean malware or as a file unknowingly downloaded from a compromised site. It collects basic information such as OS version information and system name, and it allows for remote operations including searching, reading, writing, moving and executing files.




















Add Comment