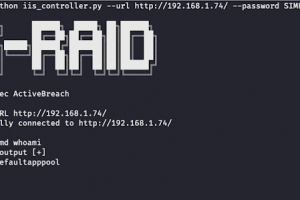
[sc name=”ad_1″] IS Raid is a native IIS module that abuses the extendibility of IIS to backdoor the web server and carry out custom actions...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] Undetectable Reverse shell & Xor encrypting with custom KEY(FUD Metasploit Rat) bypass Top Antivirus like...
[sc name=”ad_1″] Capture user screenshots using shortcut file (Bypass SmartScreen/Defender). Suport Multi-monitor Legal disclaimer: Usage of...
[sc name=”ad_1″] VBScript minifier Features Remove extra whitespace Trailing whitespace Leading whitespace Blank lines Inline extra spaces Remove...
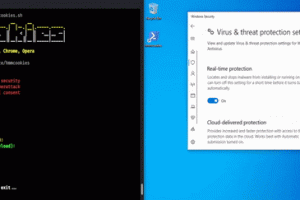
[sc name=”ad_1″] Grab cookies from Firefox, Chrome, Opera using a shortcut file (bypass UAC) Legal disclaimer: Usage of HMMCOOKIES for attacking...
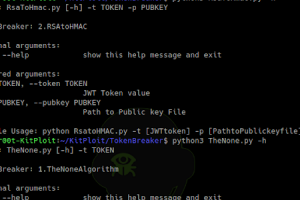
[sc name=”ad_1″] Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None Algorithm RSAtoHMAC Refer to this link about...
[sc name=”ad_1″] Capturing audio (.wav) from target using a link How it works? After the user grants microphone permissions, a website redirect...
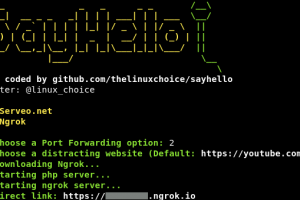
[sc name=”ad_1″] Script to generate an Android App to track location in real time Features: Custom App Name 2 Port Forwarding options (Ngrok or...
[sc name=”ad_1″] SGN is a polymorphic binary encoder for offensive security purposes such as generating statically undetecable binary payloads. It...
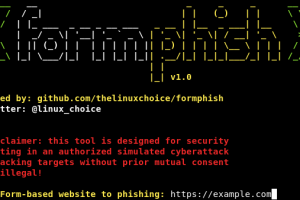
[sc name=”ad_1″] Auto Phishing form-based websites. This tool can automatically detect inputs on html form-based websites to create a phishing page...