[sc name=”ad_1″] Set of tools for creating/injecting payload into images. Useful references for better understanding of pixload and its use-cases:...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] Background A while back I was challenged to write a discovery tool with Python3 that could automate the process of finding...
[sc name=”ad_1″] OpenCTI is an open source platform allowing organizations to manage their cyber threat intelligence knowledge and observables. It...
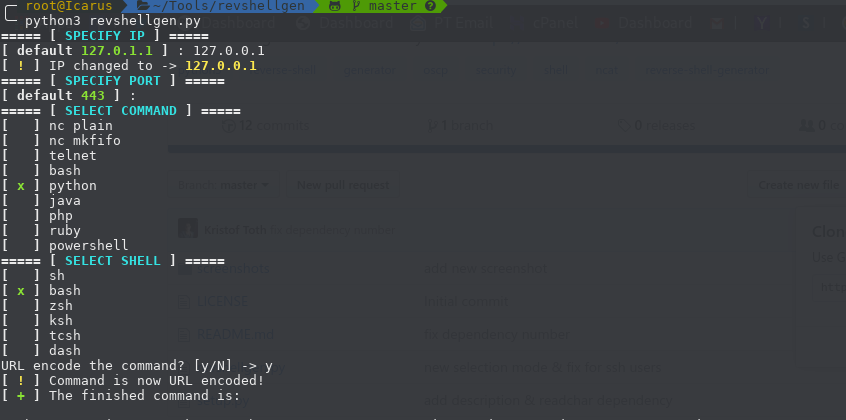
[sc name=”ad_1″] Standalone python script for generating reverse shells easily and automating the boring stuff like URL encoding the command and...
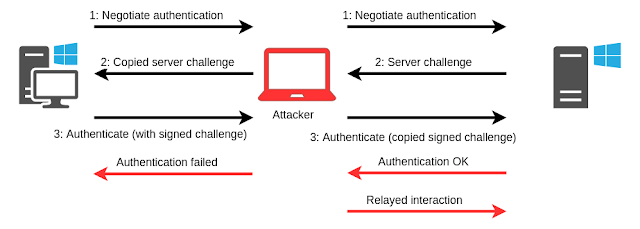
[sc name=”ad_1″] POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin. Requirements These tools require impacket...
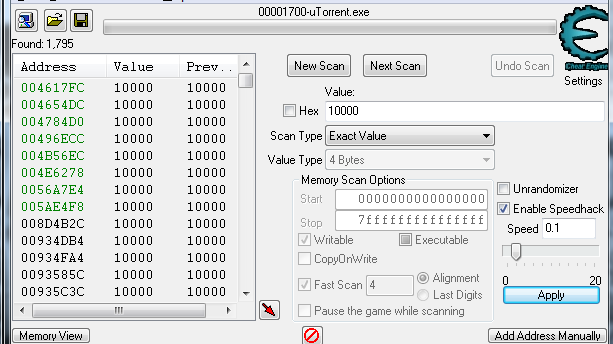
[sc name=”ad_1″] Cheat Engine is an open source tool designed to help you with modifying single player games running under window so you can make...
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
[sc name=”ad_1″] A low interaction honeypot with the capability to be more of a medium interaction honeypot. HoneyPy is written in Python2 and is...
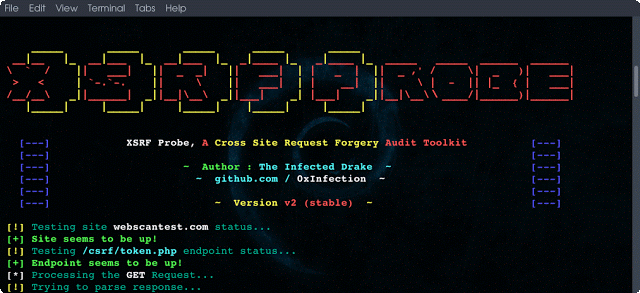
[sc name=”ad_1″] XSRFProbe is an advanced Cross Site Request Forgery (CSRF/XSRF) Audit and Exploitation Toolkit. Equipped with a Powerful Crawling...
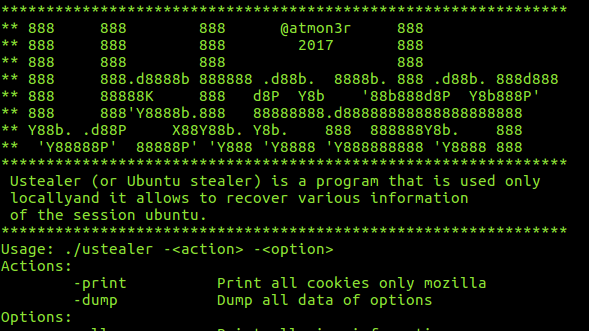
[sc name=”ad_1″] Ubuntu stealer, steal ubuntu information in local pc (nice with usb key) Require G++ sudo apt-get install g++ libsqlite3 sudo apt...