[sc name=”ad_1″] CryptonDie is a ransomware developed for study purposes. Options --key key used to encrypt and decrypt files, default is random...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] HRShell: An advanced HTTP(S) Reverse Shell built with Flask HRShell is an HTTPS/HTTP reverse shell built with flask. It’s...
[sc name=”ad_1″] Clone me! Clone or download the project: git clone SecurityNotFound cd SecurityNotFound “Installation” The src/404.php...
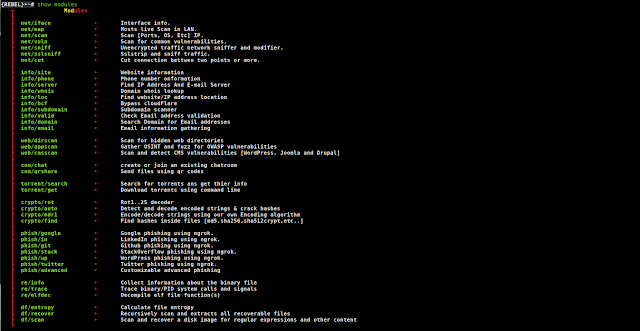
[sc name=”ad_1″] Rebel framework is an advanced and easy to use penetration testing framework.You can use it to automate the automation itself...
[sc name=”ad_1″] A File Inclusion & Directory Traversal fuzzing, enumeration & exploitation tool. FDsploit menu: $ python fdsploit.py -h...
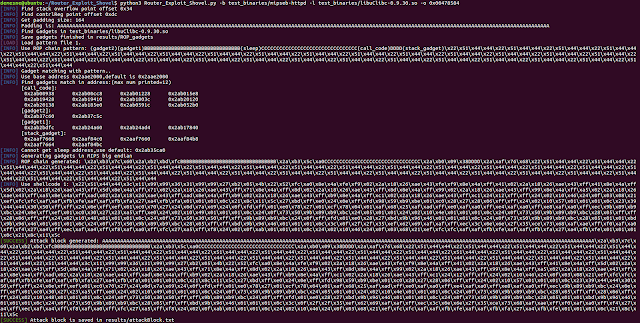
[sc name=”ad_1″] Automated Application Generation for Stack Overflow Types on Wireless Routers. Router exploits shovel is an automated application...
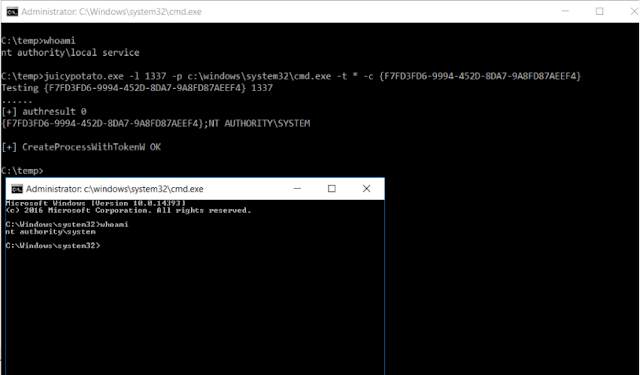
[sc name=”ad_1″] A sugared version of RottenPotatoNG, with a bit of juice, i.e. another Local Privilege Escalation tool, from a Windows Service...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly...
[sc name=”ad_1″] Aura Botnet C2 Server The botnet’s C2 server utilizes the Django framework as the backend. It is far from the most efficient...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an...