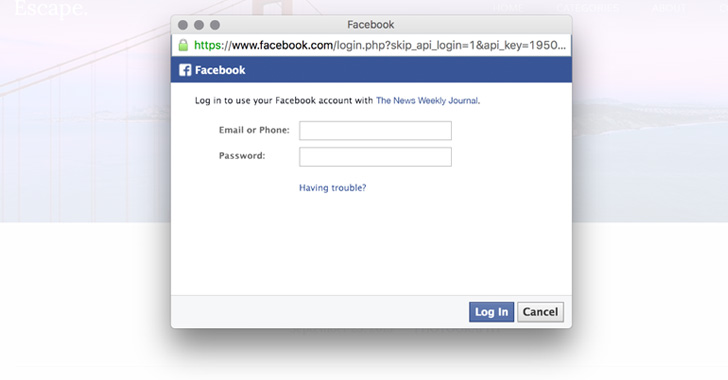
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
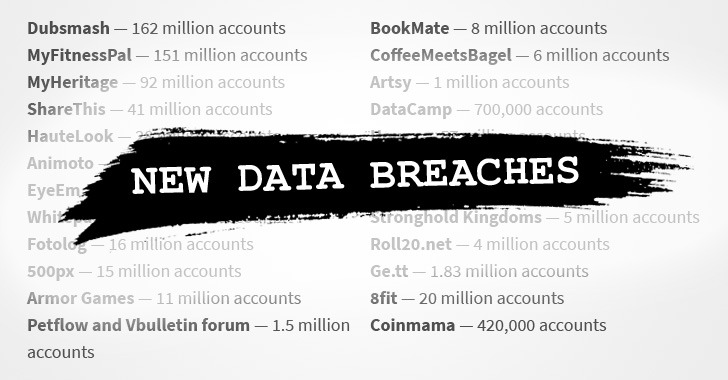
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second...
[sc name=”ad_1″] The United States Department of Justice has announced espionage charges against a former US Air Force intelligence officer with...
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
[sc name=”ad_1″] Cybersecurity researchers have discovered a way to hide malicious code in Intel SGX enclaves, a hardware-based memory encryption...
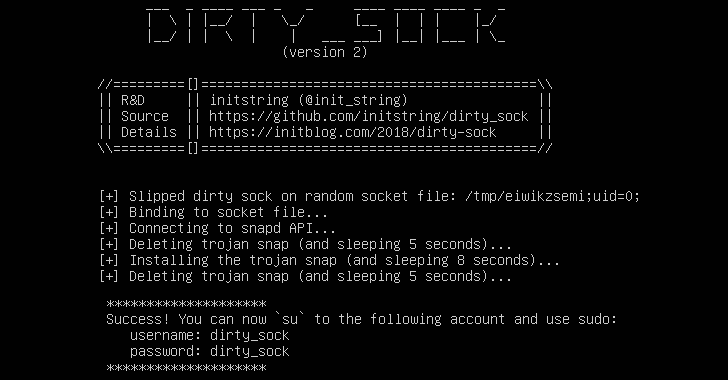
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
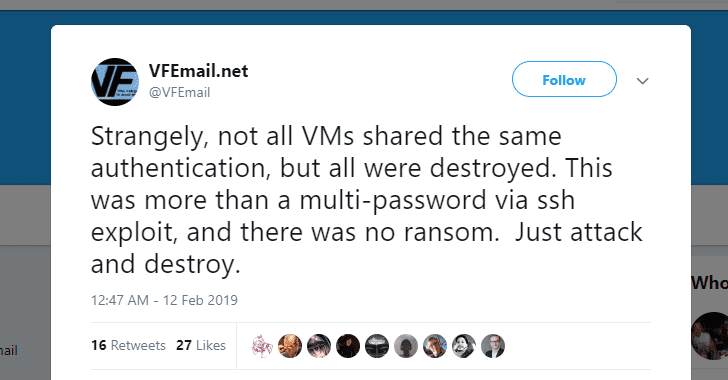
[sc name=”ad_1″] What could be more frightening than a service informing you that all your data is gone—every file and every backup servers are...
[sc name=”ad_1″] Welcome back! Adobe has today released its monthly security updates to address a total of 75 security vulnerabilities across its...
[sc name=”ad_1″] A new security vulnerability has been discovered in the latest version of Apple’s macOS Mojave that could allow a malicious...
[sc name=”ad_1″] Microsoft has issued its second Patch Tuesday for this year to address a total of 77 CVE-listed security vulnerabilities in its...