[sc name=”ad_1″] This is why you should always think twice before opening innocent looking email attachments, especially word and pdf files...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
[sc name=”ad_1″] Here we have great news for all bug bounty hunters. Now you can get paid up to $40,000 for finding and responsibly reporting...
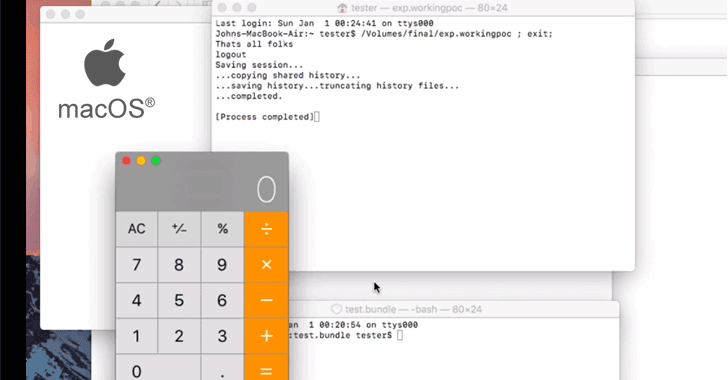
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
[sc name=”ad_1″] The United States Postal Service has patched a critical security vulnerability that exposed the data of more than 60 million...
[sc name=”ad_1″] A widely used third-party NodeJS module with nearly 2 million downloads a week was compromised after one of its open-source...
[sc name=”ad_1″] Cheetah Mobile—a prominent Chinese app company, known for its popular utility apps like Clean Master and Battery Doctor—and one of...
[sc name=”ad_1″] British and Dutch data protection regulators Tuesday hit the ride-sharing company Uber with a total fine of $1,170,892 (~ 1.1...
[sc name=”ad_1″] Google, the FBI, ad-fraud fighting company WhiteOps and a collection of cyber security companies worked together to shut down one...
[sc name=”ad_1″] The Department of Justice announced Wednesday charges against two Iranian nationals for their involvement in creating and...