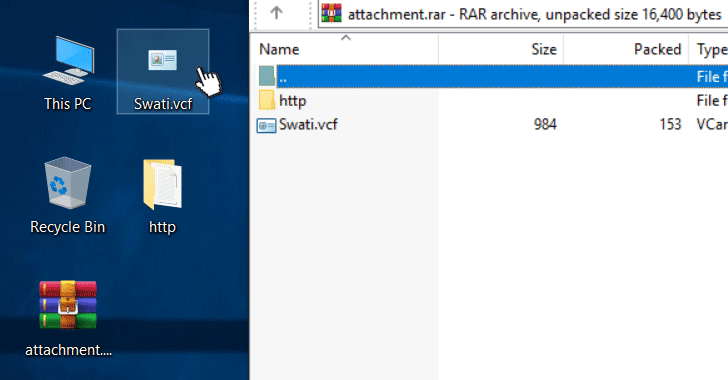
[sc name=”ad_1″] A zero-day vulnerability has been discovered and reported in the Microsoft’s Windows operating system that, under a certain...
Category - Articles
Latest Articles related to Cyber Security, Penetration Testing and Technology.
[sc name=”ad_1″] If you are responsible for the cybersecurity of a medium-sized company, you may assume your organization is too small to be...
[sc name=”ad_1″] Good news, the new Kickass Torrents site is back. Back in July 2017, popular BitTorrent site Kickass Torrents (KAT cr) was taken...
[sc name=”ad_1″] Remember “The Shadow Brokers” and the arrest of a former NSA contractor accused of stealing 50 Terabytes of top secret...
[sc name=”ad_1″] If your computer has been infected with PyLocky Ransomware and you are searching for a free ransomware decryption tool to unlock...
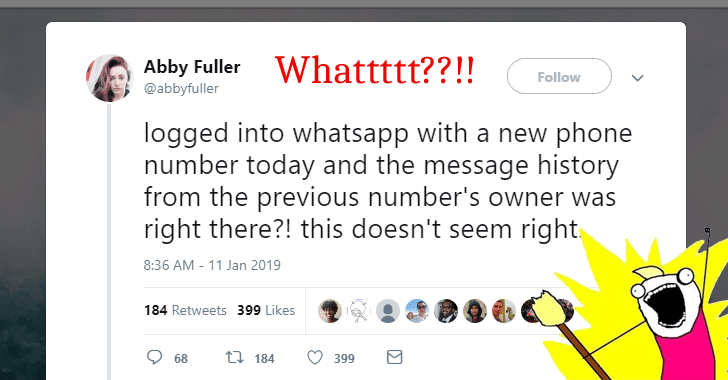
[sc name=”ad_1″] In-short conclusion—Whatsapp service or its 45-days deletion policy doesn’t seem to have a bug. For detailed logical...
[sc name=”ad_1″] A simple DDoS attack could land you in jail for 10 years or even more. A Massachusetts man has been sentenced to over 10 years in...
[sc name=”ad_1″] Almost every activity on the Internet starts with a DNS query, a key function of the Internet that works as an Internet’s...
[sc name=”ad_1″] Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux...
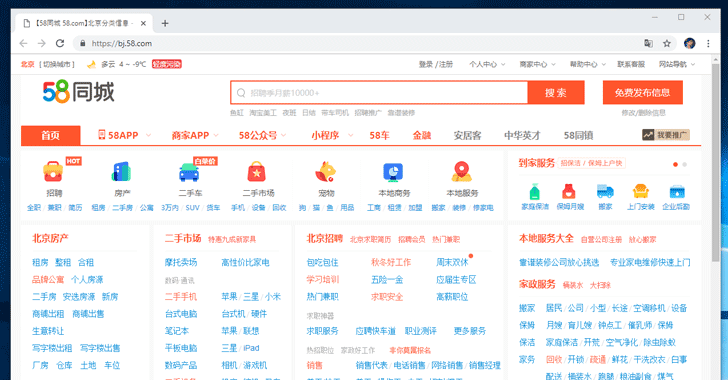
[sc name=”ad_1″] Cybersecurity researcher has discovered online a massive database containing records of more than 202 million Chinese citizens...