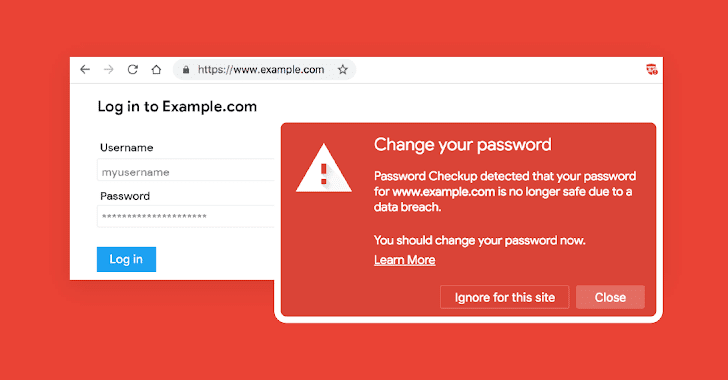
[sc name=”ad_1″] With so many data breaches happening almost every week, it has become difficult for users to know if their credentials are already...
Author - Mazen Elzanaty
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
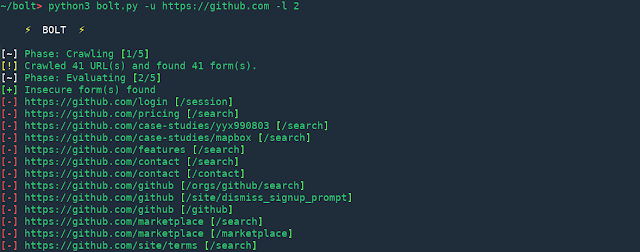
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...
[sc name=”ad_1″] Bolt is in beta phase of development which means there can be bugs. Any production use of this tool discouraged. Pull requests and...
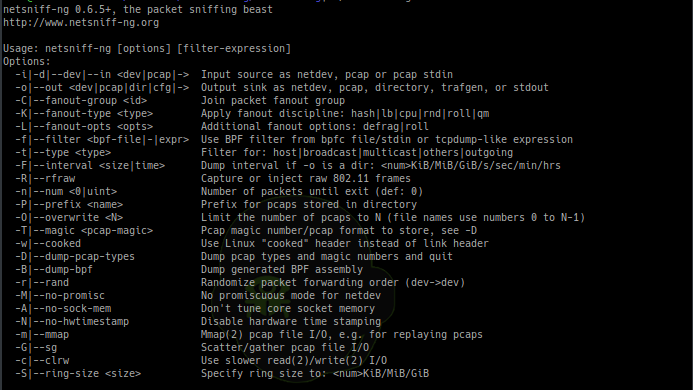
[sc name=”ad_1″] netsniff-ng is a free Linux networking toolkit, a Swiss army knife for your daily Linux network plumbing if you will. Its gain of...
[sc name=”ad_1″] A 20-year-old college student who stole cryptocurrency worth more than $5 million by hijacking victims’ phone numbers has...
[sc name=”ad_1″] Just because an app is available on Google Play Store doesn’t mean that it is a legitimate app. Despite so many efforts by...
[sc name=”ad_1″] QuadrigaCX, the largest bitcoin exchange in Canada, has claimed to have lost CAD 190 million (nearly USD 145 million) worth of...
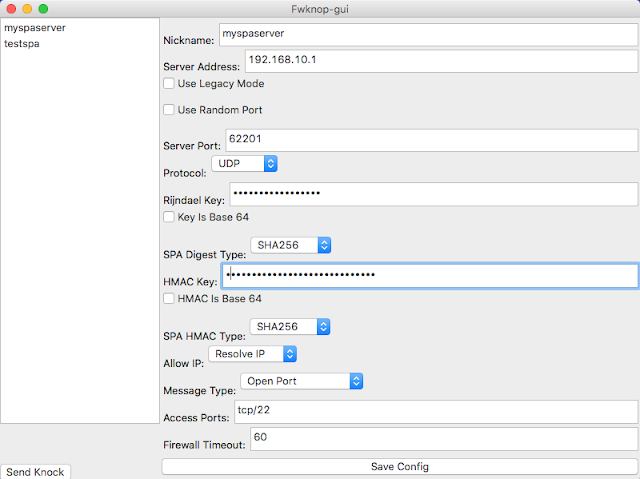
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] Many of you might have this question in your mind: “Is it illegal to test a website for vulnerability without permission...