Wazuh is a security detection, visibility, and compliance open source project. It was born as a fork of OSSEC HIDS, later was integrated with Elastic Stack and OpenSCAP evolving into a more comprehensive solution.
Wazuh helps you to gain deeper security visibility into your infrastructure by monitoring hosts at an operating system and application level. This solution, based on lightweight multi-platform agents, provides the following capabilities:
- Log management and analysis: Wazuh agents read operating system and application logs, and securely forward them to a central manager for rule-based analysis and storage.
- File integrity monitoring: Wazuh monitors the file system, identifying changes in content, permissions, ownership, and attributes of files that you need to keep an eye on.
- Intrusion and anomaly detection: Agents scan the system looking for malware, rootkits or suspicious anomalies. They can detect hidden files, cloaked processes or unregistered network listeners, as well as inconsistencies in system call responses.
- Policy and compliance monitoring: Wazuh monitors configuration files to ensure they are compliant with your security policies, standards or hardening guides. Agents perform periodic scans to detect applications that are known to be vulnerable, unpatched, or insecurely configured.
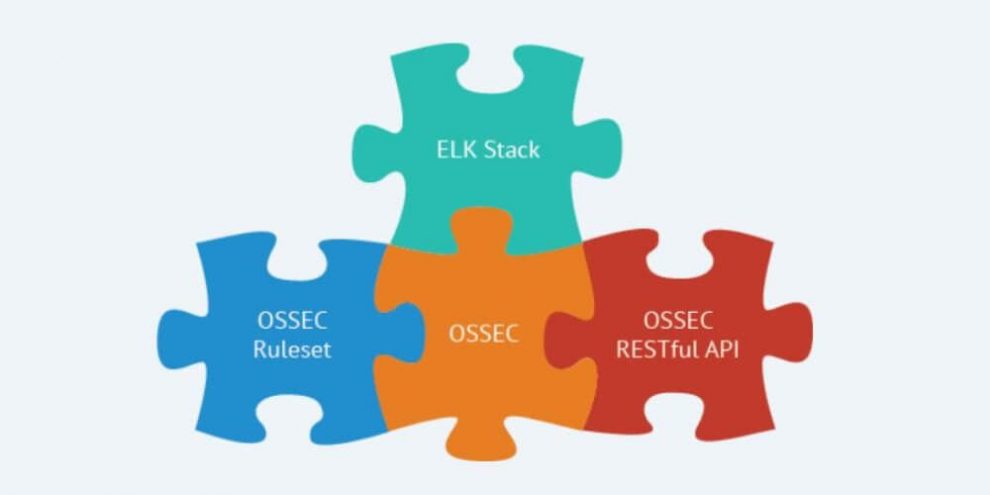
This diverse set of capabilities is provided by integrating OSSEC, OpenSCAP and Elastic Stack, making them work together as a unified solution, and simplifying their configuration and management. Wazuh provides an updated log analysis ruleset, and a RESTful API that allows you to monitor the status and configuration of all Wazuh agents. Wazuh also includes a rich web application (fully integrated as a Kibana app), for mining log analysis alerts and for monitoring and managing your Wazuh infrastructure.
Software and libraries used
- Modified version of Zlib and a small part of OpenSSL (SHA1 and Blowfish libraries).
- OpenSSL Project for use in the OpenSSL Toolkit (http://www.openssl.org/).
- Cryptographic software written by Eric Young ([email protected]).
- Software developed by the Zlib project (Jean-loup Gailly and Mark Adler).
- Software developed by the cJSON project (Dave Gamble).
- Node.js (Ryan Dahl).
- NPM packages Body Parser, Express, HTTP-Auth and Moment.
OSSEC HIDS
OSSEC HIDS is a Host-based Intrusion Detection System (HIDS) used both for security detection, visibility, and compliance monitoring. It’s based on a multi-platform agent that forwards system data (e.g log messages, file hashes, and detected anomalies) to a central manager, where it is further analyzed and processed, resulting in security alerts. Agents convey event data to the central manager via a secure and authenticated channel.
Additionally, OSSEC HIDS provide a centralized syslog server and an agentless configuration monitoring system, providing security insight into the events and changes on agentless devices such as firewalls, switches, routers, access points, network appliances, etc.
OpenSCAP
OpenSCAP is an OVAL (Open Vulnerability Assessment Language) and XCCDF (Extensible Configuration Checklist Description Format) interpreter used to check system configurations and to detect vulnerable applications.
It’s a well-known tool designed to check the security compliance and hardening of the systems using industry standard security baselines for enterprise environments.
Elastic Stack
Elastic Stack is a software suite (Filebeat, Logstash, Elasticsearch, Kibana) used to collect, parse, index, store, search, and present log data. It provides a web frontend useful for gaining a high-level dashboard view of events, as well to realize advanced analytics and data mining deep into your store of event data.
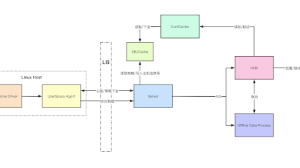
Wazuh installation involves two central components, the Wazuh server, and Elastic Stack. In addition, Wazuh agents will need to be deployed to the monitored hosts in your environment:
- Wazuh server: Runs the Wazuh manager, API and Filebeat (only necessary in distributed architecture). Collects and analyzes data from deployed agents.
- Elastic Stack: Runs the Elasticsearch engine, Logstash server and Kibana (including the Wazuh App). It reads, parses, indexes, and stores alert data generated by the Wazuh server.
- Wazuh agent: Runs on the monitored host, collecting system log and configuration data, and detecting intrusions and anomalies. It talks with the Wazuh server, to which it forwards collected data for further analysis.
Distributed architectures do run the Wazuh server and Elastic Stack cluster (one or more servers) on different hosts. On the other hand, single-host architectures have Wazuh server and Elastic Stack installed in the same system.


















Add Comment