[sc name=”ad_1″] Google has launched a new encryption algorithm that has been built specifically to run on mobile phones and smart IoT devices that...
Archive - February 2019
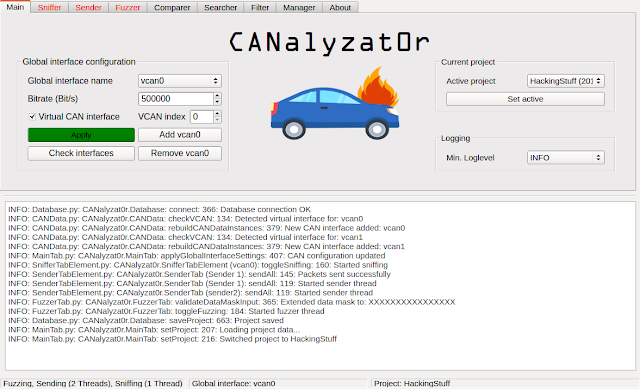
[sc name=”ad_1″] This software project is a result of a Bachelor’s thesis created at SCHUTZWERK in collaboration with Aalen University by...
[sc name=”ad_1″] The developers behind the privacy-minded Zcash cryptocurrency have recently discovered and patched a highly dangerous...
[sc name=”ad_1″] For all of the undeniable conveniences the Internet has brought us, it’s becoming an increasingly dangerous place to be...
[sc name=”ad_1″] Using an Android device? Beware! You have to remain more caution while opening an image file on your smartphone—downloaded...
[sc name=”ad_1″] Synopsis bscan is a command-line utility to perform active information gathering and service enumeration. At its core, bscan...
[sc name=”ad_1″] Ever sent a message on Facebook Messenger then immediately regretted it, or an embarrassing text to your boss in the heat of the...
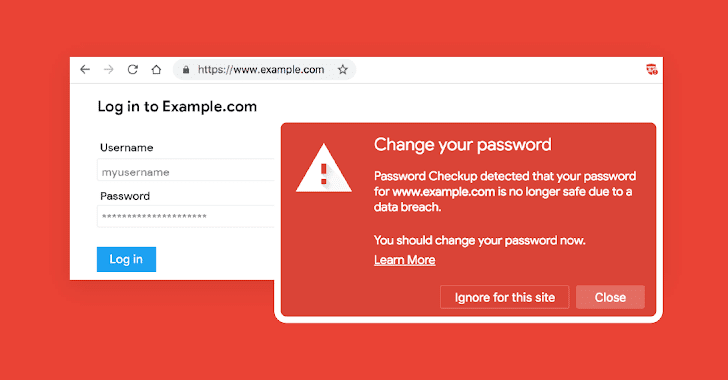
[sc name=”ad_1″] With so many data breaches happening almost every week, it has become difficult for users to know if their credentials are already...
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...