[sc name=”ad_1″]
We knew that there are already tools doing this, for example Wappalyzer or CERN’s WAD,
but we wanted a modular tool capable of reading Wappalyzer database as well as an user-supplied one, since we often encounter new or custom web-frameworks.
For this reason we developed the detection of uncommon HTTP Headers, which are not in the technologies database yet.
Since during our penetration tests we heavily use Portswigger Burp, we also integrated WebTech in Burp’s passive and active scanners so you can use it directly as a Burp Extension.
CLI Installation
WebTech is available on pip:
pip install webtechIt can be also installed via setup.py:
python setup.py install --userBurp Integration
Download Jython 2.7.0 standalone and install it into Burp.
In “Extender” > “Options” > “Python Environment”:
- Select the Jython jar location
Finally, in “Extender” > “Extension”:
- Click “Add”
- Select “py” or “Python” as extension format
- Select the
Burp-WebTech.pyfile in this folder
Usage
Scan a website:
$ webtech -u https://example.com/
Target URL: https://example.com
...
$ webtech -u file://response.txt
Target URL:
...
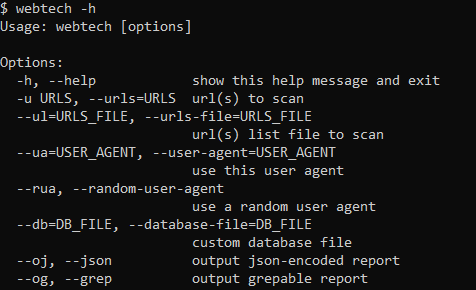
Full usage:
$ webtech -h
Usage: webtech [options]
Options:
-h, --help show this help message and exit
-u URLS, --urls=URLS url(s) to scan
--ul=URLS_FILE, --urls-file=URLS_FILE
url(s) list file to scan
--ua=USER_AGENT, --user-agent=USER_AGENT
use this user agent
--rua, --random-user-agent
use a random user agent
--db=DB_FILE, --database-file=DB_FILE
custom database file
--oj, --json output json-encoded report
--og, --grep output grepable report
Resources for database matching
HTTP Headers information – http://netinfo.link/http/headers.html
Cookie names – https://webcookies.org/top-cookie-names


















Add Comment