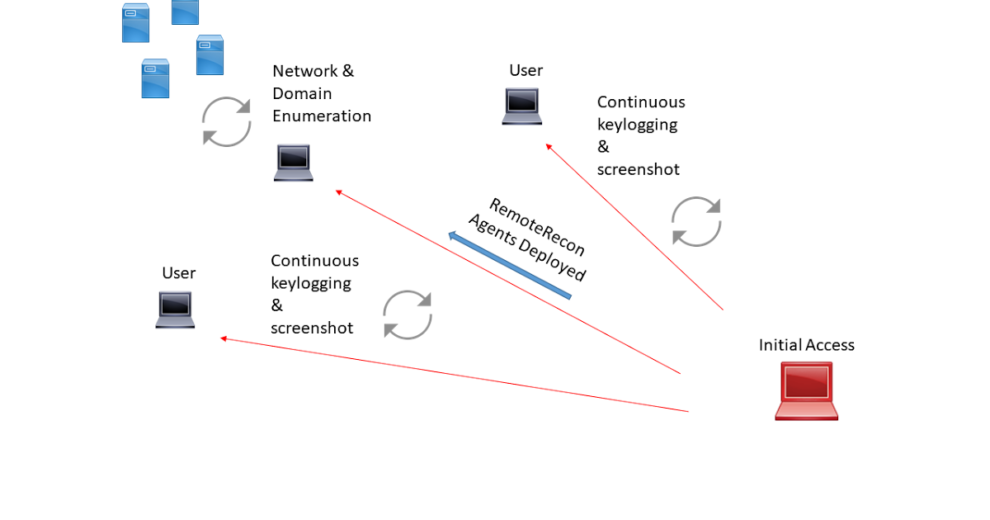
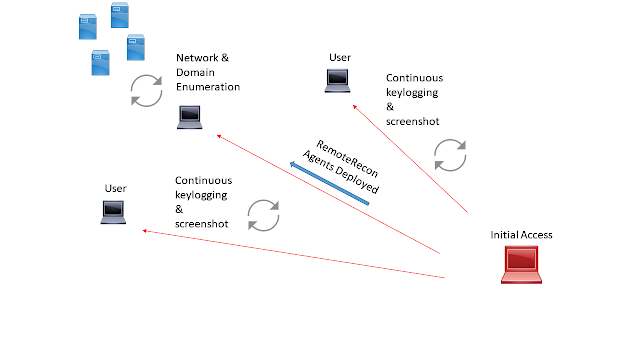
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often times as operator’s we need to compromise a host, just so we can keylog or screenshot (or some other miniscule task) against a person/host of interest. Why should you have to push over beacon, empire, innuendo, meterpreter, or a custom RAT to the target? This increases the footprint that you have in the target environment, exposes functionality in your agent, and most likely your C2 infrastructure. An alternative would be to deploy a secondary agent to targets of interest and collect intelligence. Then store this data for retrieval at your discretion. If these compromised endpoints are discovered by IR teams, you lose those endpoints and the information you’ve collected, but nothing more. Below is a visual representation of how an adversary would utilize this.
- Visual Studio 2015+
- Windows 7 and .NET SDK
- Windows 8.1 SDK
- mscorlib.tlh (This is included in the project but there are instances where intellisense can’t seem to find it [shrug])
- .NET 3.5 & 4
- James Forshaw’s DotNetToJScript project
- Fody/Costura Nuget package. Package and embed any extra dependencies in .NET.
For a short setup guide, please visit the wiki
Also check https://pentesttools.net/2018/06/22/crypto-identifier-tool-to-uncipher-data-using-multiple-algorithms-and-block-chaining-modes/



















Add Comment