New Linux Privilege Escalation Tool.
Getting Started
- System Information Gatherer
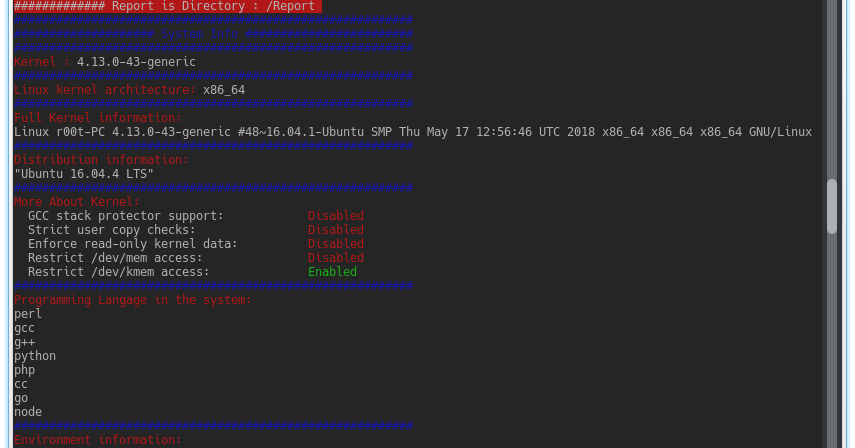
- Kernel Information Gatherer
- Checking Development environments on the system (Escaping Restricted Shells)
- Extract PATH & environment Information
- Check Kernel if Vulnerable To Dirty cow Exploit
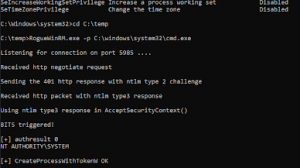
- Password Collector
- Log Analyzer For interesting Information
- Check Password Policy
- Database Password Collector
- Check If SSH Are Allowed With Root
- Checking For interesting Root,Home,Var Directory Files
- RSA Key’s Collector
- Command History Analyzer
- Users Enumeration (Root – Sudo – UID List – GID List)
- Cron Jobs Enumeration (Permissions – Own Cron – Cron Content – Writable Cron)
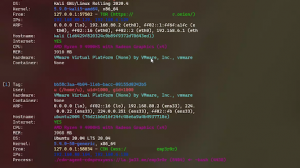
- Network Information Lookup (TCP Connections – ARP – Services)
- List Are Open For Updates 🙂


















Add Comment