On Wednesday, Microsoft has released a patch for the Microsoft Malware Protection Engine (MPE) to fix a critical severity remote code execution (RCE) flaw in it.
The vulnerability (tracked as CVE-2017-11937) has been discovered by UK’s National Cyber Security Centre (NCSC) that could lead to memory corruption and enable an attacker to execute arbitrary code to gain control over the affected computer.
According to Microsoft:
A remote code execution vulnerability exists when the Microsoft Malware Protection Engine does not properly scan a specially crafted file, leading to memory corruption. An attacker who successfully exploited this vulnerability could execute arbitrary code in the security context of the LocalSystem account and take control of the system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights.
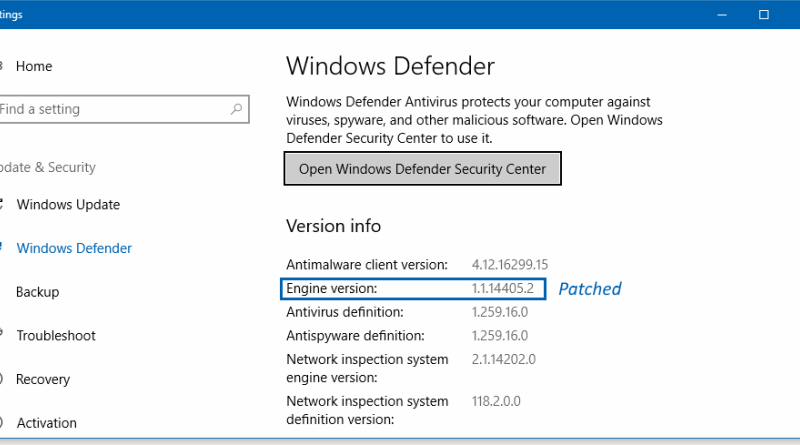
To exploit this flaw, a specially crafted file needs to be scanned by a vulnerable version (the last affected version is 1.1.14306.0) of the Microsoft Malware Protection Engine. There are several methods that an attacker could set a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For instance, an attacker can use a website to present a specifically crafted file to the user’s system that is scanned when the website is visited by the user.
Microsoft has published an update to fix the way in which the Microsoft Malware Protection Engine scans specially crafted files. The update will be delivered automatically to the affected systems and no action is needed.




















Add Comment