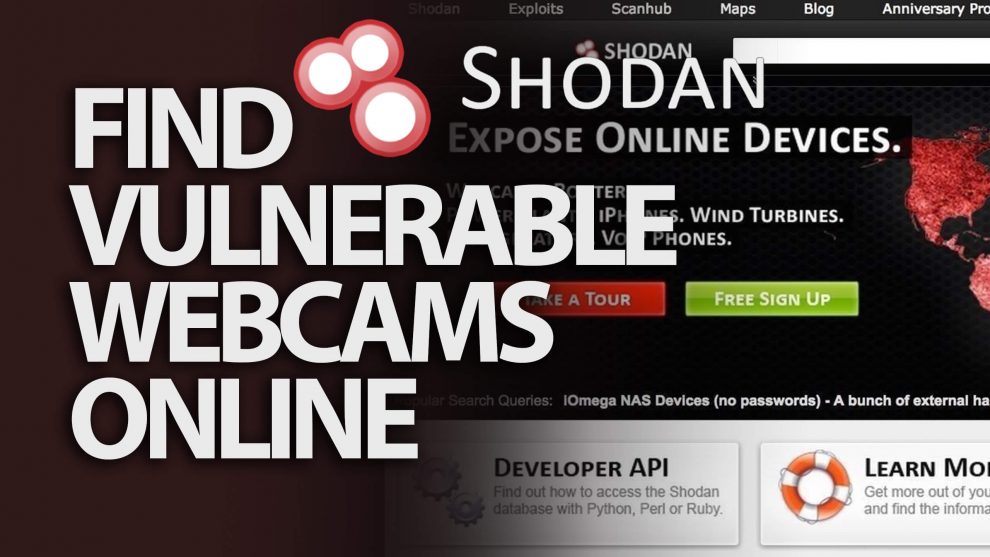
Shodan is a search engine that lets the user find specific types of computers (
Shodan collects data mostly on web servers (HTTP/HTTPS – port 80, 8080, 443, 8443), as well as FTP (port 21), SSH (port 22), Telnet (port 23), SNMP (port 161), IMAP (port 993), SIP (port 5060), and Real Time Streaming Protocol (RTSP, port 554). The latter can be used to access webcams and their video stream.
Default Webcam Username & Passwords
Although some of these webcams are unprotected, many of them will require authentication. The first step is to try the default username and password. I have compiled a short list of the default username and passwords of some of the most widely used webcams below.
- ACTi: admin/123456 or Admin/123456
- Axis (traditional): root/pass,
- Axis (new): requires password creation during first login
- Cisco: No default password, requires creation during first login
- Grandstream: admin/admin
- IQinVision: root/system
- Mobotix: admin/meinsm
- Panasonic: admin/12345
- Samsung Electronics: root/root or admin/4321
- Samsung Techwin (old): admin/1111111
- Samsung Techwin (new): admin/4321
- Sony: admin/admin
- TRENDnet: admin/admin
- Toshiba: root/ikwd
- Vivotek: root/<blank>
- WebcamXP: admin/ <blank>
Video
https://www.youtube.com/watch?v=UB-wCbOoz1Q&feature=youtu.be



















Add Comment