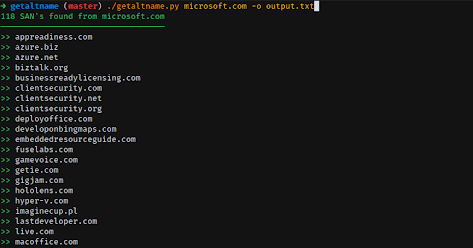
GetAltName it’s a little script that can extract Subject Alt Names for SSL Certificates directly from HTTPS web sites which can provide you with DNS names or virtual servers.
It’s useful in a discovery phase of a pen-testing assessment, this tool can provide you with more information about your target and scope.
This code is in alpha stage and has been rewritten from Ruby to Python, it doesn’t do as much as it should. lots of things and features are missing, but it delivers, treat it as a quick-dirty-code. More features incoming, also you’re welcome to contribute if you want.
You can read more about how this tool works from my post in getroot.info (in Spanish).
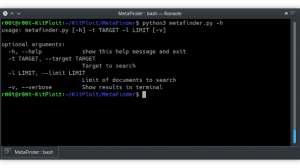
Usage:
usage: getaltname.py [-h] [-p PORT] [-s [timeout]] [-m] [-o OUTPUT] [-c {l,s}]
[-d]
hostname
positional arguments:
hostname Host to analyze.
optional arguments:
-h, --help show this help message and exit
-p PORT, --port PORT Destiny port (default 443)
-s [timeout], --search-crt [timeout] Retrieve subdomains found in crt.sh
-m, --matching-domain Show matching domain name only
-o OUTPUT, --output OUTPUT Set output filename
-c {l,s}, --clipboard {l,s} Copy the output to the clipboard as a
List or a Single string
-d, --debug Set debug enableYou can output to a text file and also copy the output to you clipboard as a List or a Single line string, which is useful if you’re trying to make a quick scan with Nmap or other tools.
Installation
Required libraries:
- colorama
- ndg-httpsclient
- pyperclip
- requests
- tldextract
Installation with pipenv:
$ git clone https://github.com/franccesco/getaltname.git
$ pipenv installInstallation with Pip:
$ git clone https://github.com/franccesco/getaltname.git
$ pip install -r requirements.txtFor the copy&paste mechanism you will have to install xclip package. Debian/Ubuntu/Mint:
$ apt install xclipTO-DO
- File output
- Output to clipboard
- Clean sub-domains wildcards
- Remove duplicates
- A filter system for main domain and TLD’s.
- Add colors (so l33t. /s)
- Get additional sub-domains from crt.sh


















Add Comment