[sc name=”ad_1″]
Almost half of the fight travelers around the world were found exposed to a critical security vulnerability discovered in online flight ticket booking system that allowed remote hackers to access and modify their travel details and even claim their frequent flyer miles.
Israeli network security researcher Noam Rotem discovered the vulnerability when he booked a flight on the Israeli airline ELAL, successful exploitation of which just required victim’s PNR (Passenger Name Record) number.
The vulnerability resided in the widely used online flight booking system developed by Amadeus, which is currently being used by nearly 141 international airlines, including United Airlines, Lufthansa and Air Canada.
After booking a flight with ELAL, the traveler receives a PNR number and a unique link that allows customers to check their booking status and related information associated with that PNR.
Rotem found that merely by changing the value of the “RULE_SOURCE_1_ID” parameter on that link to someone else’s PNR number would display personal and booking-related information from the account associated with that customer.
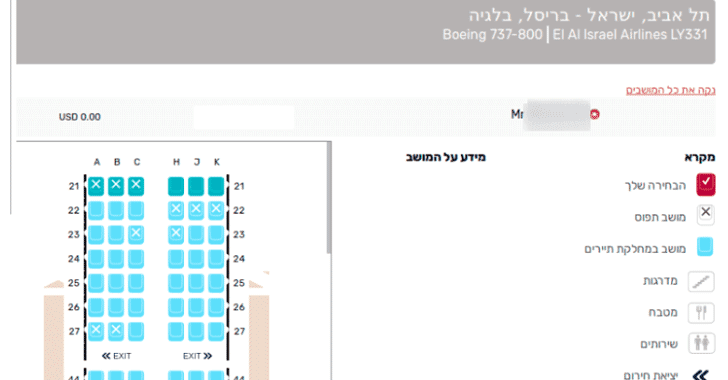
Using disclosed information, i.e. booking ID and last name of the customer, an attacker can simply access the victim’s account on ELAL’s customer portal and “make changes, claim frequent flyer miles to a personal account, assign seats and meals, and update the customer’s email and phone number, which could then be used to cancel/change flight reservation via customer service.”
“Though the security breach requires knowledge of the PNR code, ELAL sends these codes via unencrypted email, and many people even share them on Facebook or Instagram. But that’s just the tip of the iceberg,” the researcher said in his blog post.
Don’t have PNR numbers of your victims? Don’t worry.
Rotem also figured out that the Amadeus portal was not using any brute-force protection that eventually allowed attackers to attempt every alphanumeric uppercase complications using a script, as shown, to find all active PNR numbers of customers of any Amadeus-linked airline website.
“After running a small and non-threatening script to check for any brute-force protections, none of which were found, we were able to find PNRs of random customers, which included all of their personal information,” Rotem added.
You can see the video demonstration provided by the researcher to know how a simple script devised by him guessed the PNR numbers and was able to find active numbers in Amadeus.
Since the Amadeus booking system is being used by at least 141 airlines, the vulnerability could have affected hundreds of millions of travelers.
[youtube https://www.youtube.com/watch?v=yYW_N6e8Was]
After discovering the vulnerability, Rotem immediately contacted ELAL to point out the threat and suggested the airline to introduce captchas, passwords and a bot protection mechanism in order to prevent brute-force attempts.
Amadeus has now fixed the issue, and the Rotem’s script can no longer identify active PNRs as demonstrated in the above video.
Upon contacting Amadeus, the company replied, “At Amadeus, we give security the highest priority and are constantly monitoring and updating our systems. Our technical teams took immediate action, and we can now confirm that the issue is solved.”
Amadeus also added that the company has also added a Recovery PTR to strengthen security further and “prevent a malicious user from accessing travelers’ personal information.”





















Add Comment